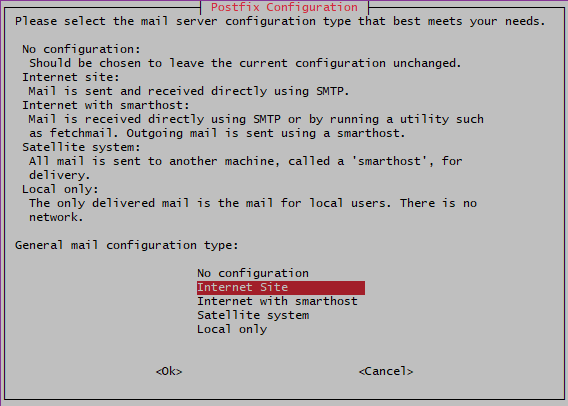
I am not sure if I selected a right configuration, probably “No configuration” is better:
ssh-keygen -t ed25519 -C "winappdev@gmail.com"
# /home/dmitriano/.ssh/id_rsa_github
# and empty passphrase
nano .ssh/config
Host github.com
HostName github.com
IdentityFile ~/.ssh/id_rsa_github
stat -c %a ~/.ssh/config
chmod 600 ~/.ssh/config
ping did not work on my clean Ubuntu 24.04 installation showing the following error:
ping developernote.com
ping: socktype: SOCK_RAW
ping: socket: Operation not permitted
ping: => missing cap_net_raw+p capability or setuid?
After updated my WordPress to 6.7.1 and added the following to wp-config.php
define( 'WP_DEBUG', true );
define( 'WP_DEBUG_LOG', true );
and got the following error message:
Fatal error: Uncaught Error: Call to undefined function wp_kses() in /home/devnote/www/wp-includes/functions.php:6098 Stack trace:
#0 /home/devnote/www/wp-includes/functions.php(5579): wp_trigger_error()
#1 /home/devnote/www/wp-includes/class-wpdb.php(1333): _deprecated_function()
#2 /home/devnote/www/wp-content/sunrise.php(11): wpdb->escape()
#3 /home/devnote/www/wp-includes/ms-settings.php(47): include_once('...')
#4 /home/devnote/www/wp-settings.php(156): require('...')
#5 /home/devnote/www/wp-config.php(107): require_once('...')
#6 /home/devnote/www/wp-load.php(50): require_once('...')
#7 /home/devnote/www/wp-blog-header.php(13): require_once('...')
#8 /home/devnote/www/index.php(17): require('...')
#9 {main} thrown in /home/devnote/www/wp-includes/functions.php on line 6098
QT generates gradle.properties with the following values:
android.useAndroidX=true
android.enableJetifier=true
androidBuildToolsVersion=34.0.0
androidCompileSdkVersion=34
androidNdkVersion=26.2.11394342
buildDir=build
qt5AndroidDir=C:/dev/libs/Qt6/android/release/arm64-v8a/./src/android/java
qtAndroidDir=C:/dev/libs/Qt6/android/release/arm64-v8a/./src/android/java
qtMinSdkVersion=23
qtTargetAbiList=arm64-v8a
qtTargetSdkVersion=33
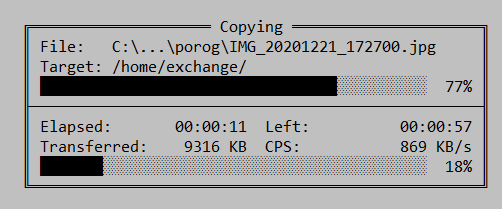
When I upload a file via SSH to my VPS server with Beeline mobile internet connection, the speed is about 300KB/sec – 800KB/sec:
sudo apt install ejabberd
ufw allow to any port 5280 proto tcp
ufw allow to any port 5222 proto tcp
ufw allow to any port 5269 proto tcp
ufw allow to any port 7777 proto tcp
sudo nano /etc/ejabberd/ejabberd.yml
##
## hosts: Domains served by ejabberd.
## You can define one or several, for example:
## hosts:
## - "example.net"
## - "example.com"
## - "example.org"
##
hosts:
- "developernote.com"
...
###. ====================
###' ACCESS CONTROL LISTS
acl:
##
## The 'admin' ACL grants administrative privileges to XMPP accounts.
## You can put here as many accounts as you want.
##
admin:
user:
- "admin": "developernote.com"
It is still possible to mine the following on GTX 1060 3GB in November 2020:
| coin | dag size | exchange |
| BTCZ | 1716MiB | https://crex24.com/ |
| ZCL | 2550MiB | https://www.hotbit.io/ |
| RVN | 2726MiB | https://www.binance.com/ |
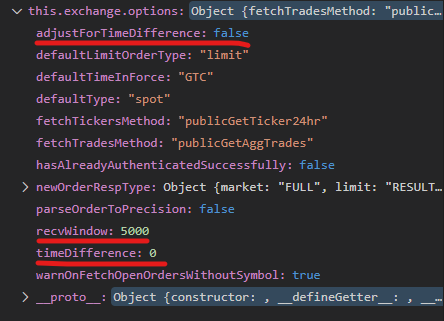
If I use CCXT on my Windows machine I periodically get ‘Timestamp for this request is outside of the recvWindow’ error.
Exchange has the following options by default: