Add Certificate Manager role
Enable probably something like Certificate Manager role on DC:
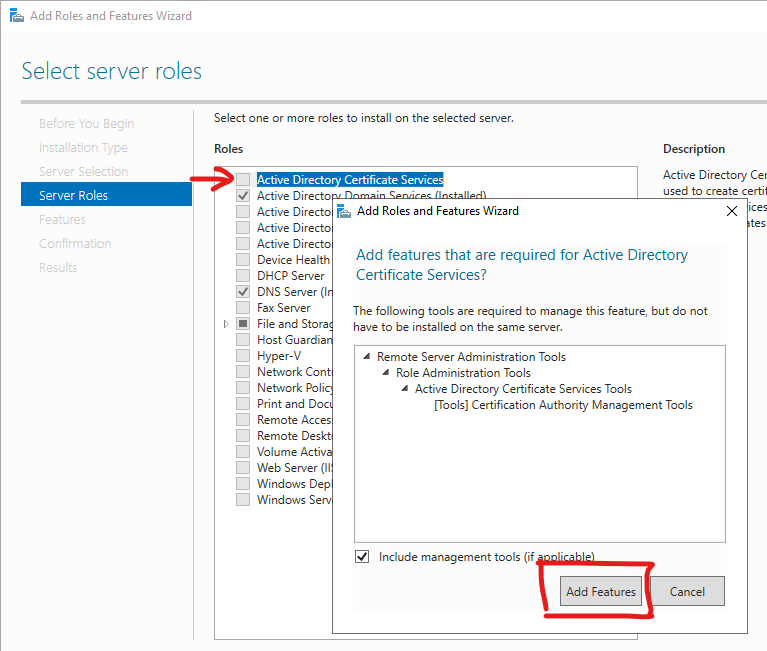
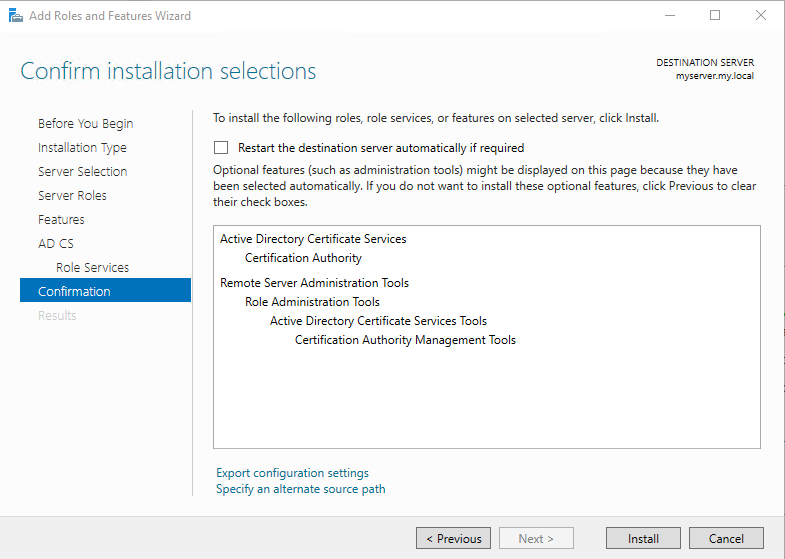
With PowerShell:
Install-WindowsFeature ADCS-Cert-Authority -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No NoChangeNeeded {}
Get-Service certsvc
Status Name DisplayName
------ ---- -----------
Stopped certsvc Active Directory Certificate Services
Install-AdcsCertificationAuthority -CAType EnterpriseRootCA
Get-Service certsvc
Status Name DisplayName
------ ---- -----------
Running certsvc Active Directory Certificate Services
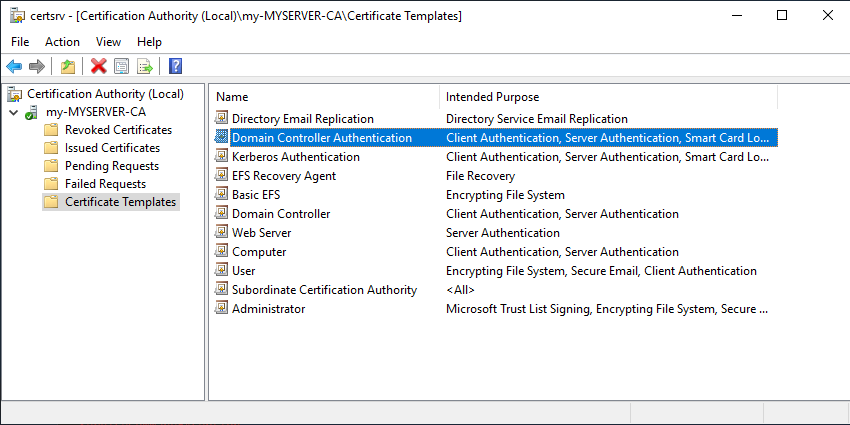
Create the certificate template
Win+R, certsrv.msc:
Win + R, mmc, File -> Add/Remove Snap-in…
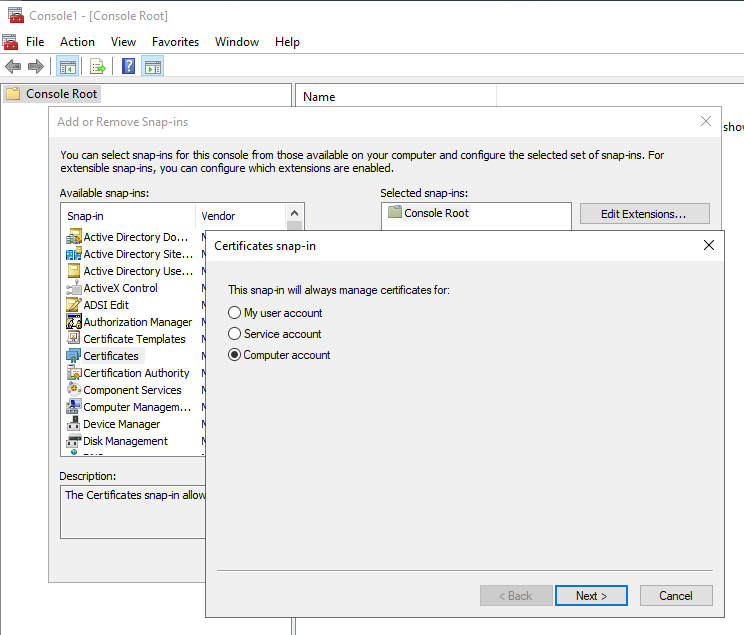
or probably better go to
and create a new certificate template:
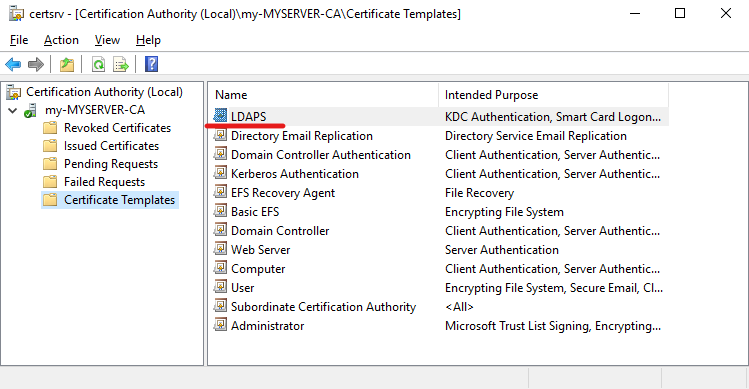
Create a new certificate
Win + R, certlm.msc:
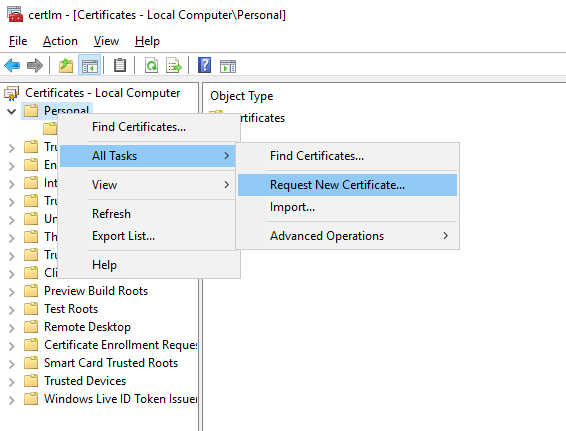
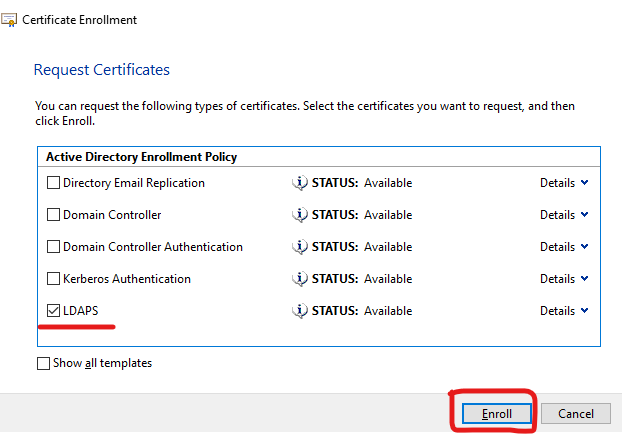
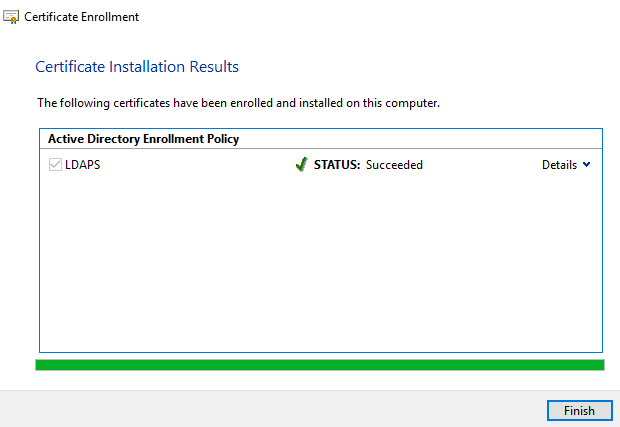
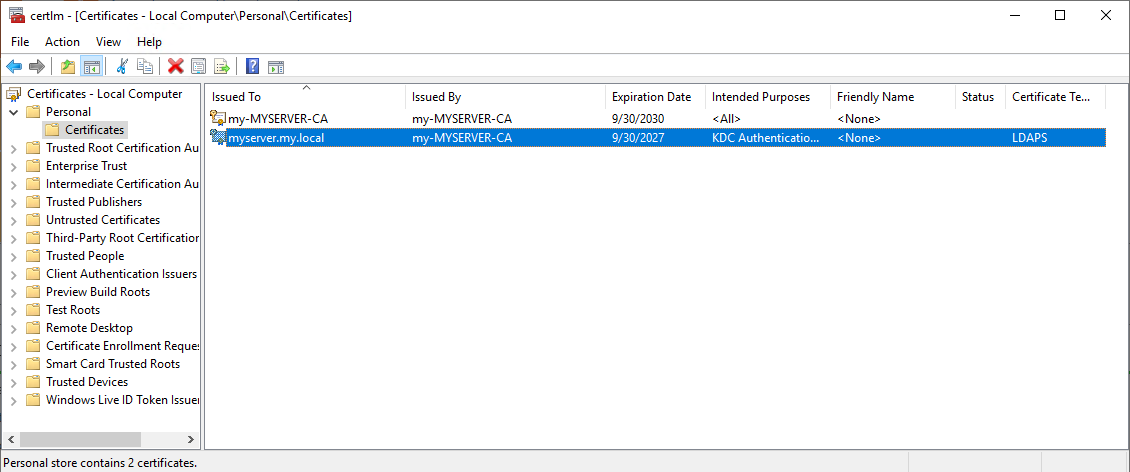
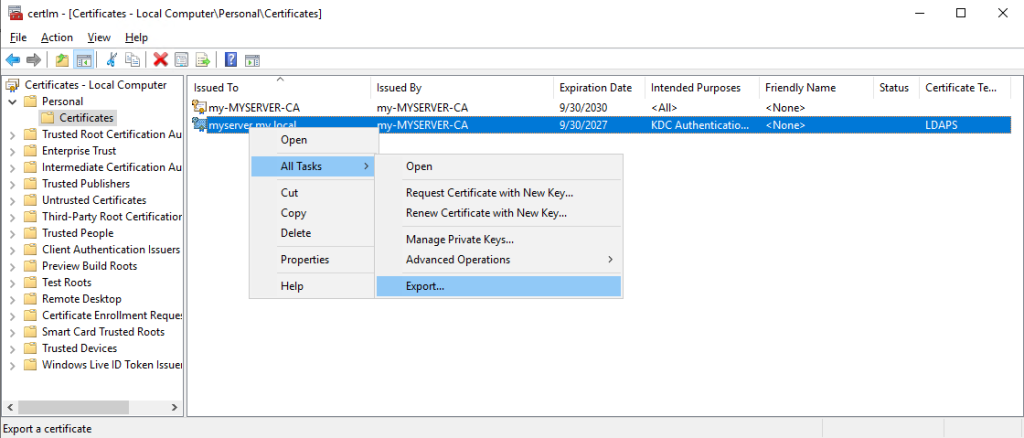
Export the certificate
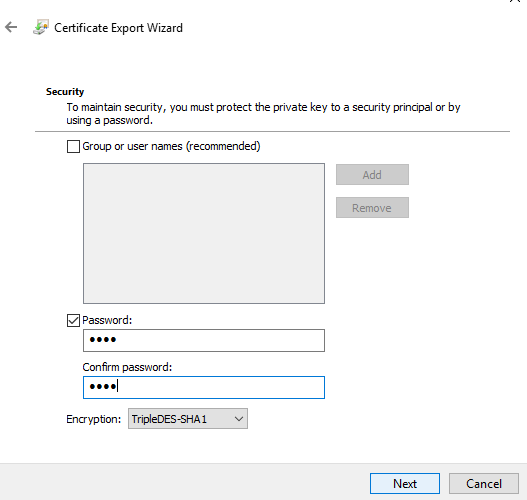
File name: C:\Users\Administrator\Downloads\ldaps.pfx
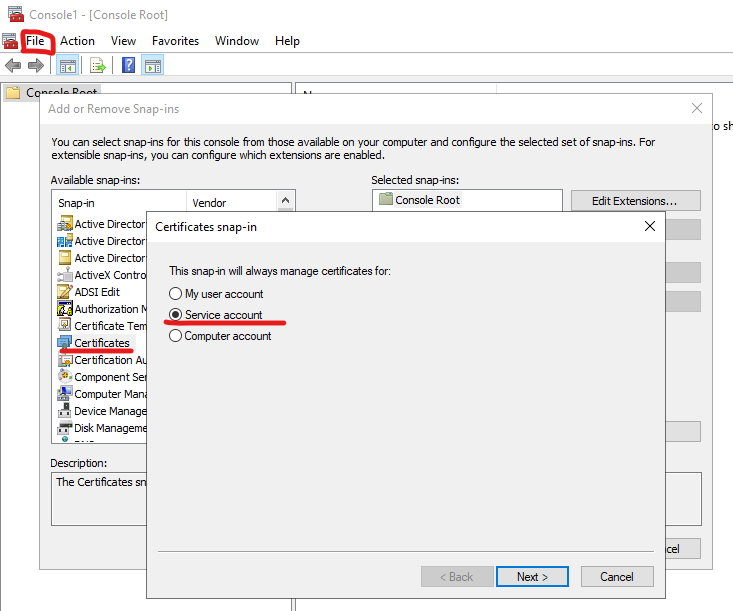
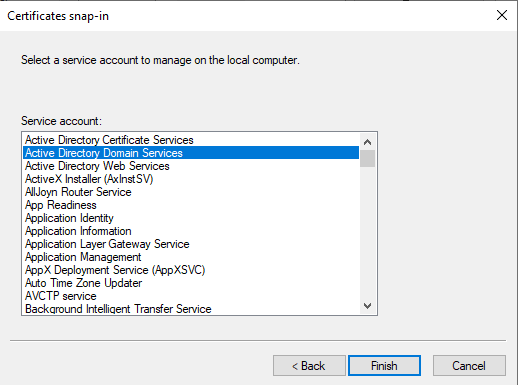
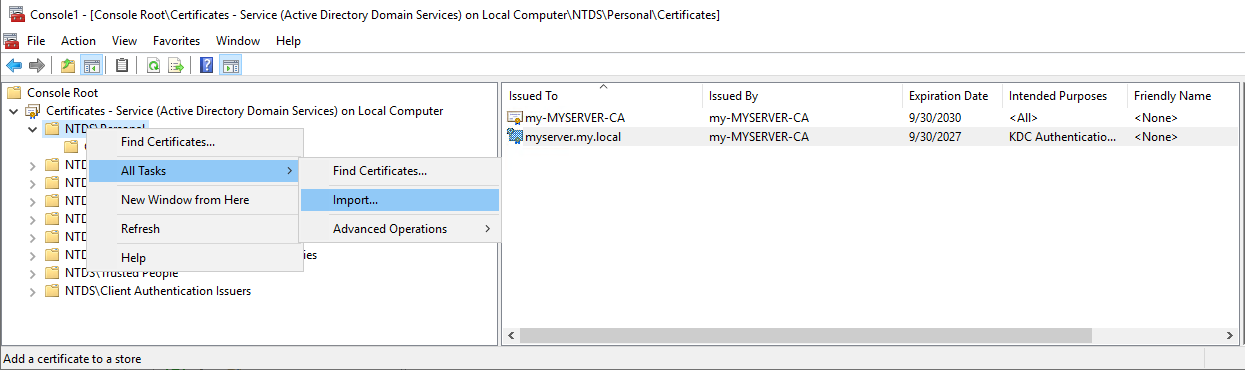
Assign the certificate to the service
Win + R, mmc:
Querying from a client machine
export ad_ip="192.168.0.123"
export ad_user="administrator@my.local"
export ad_password="1234@abc"
export LDAPTLS_REQCERT=never
ldapsearch -H ldaps://$ad_ip:636 -x -D $ad_user -w $ad_password -b "DC=my,DC=local" \
-s sub -a always -z 1000 "(objectClass=user)" "serviceClassName" "serviceDNSName" "objectClass"
Installing the certificate on Ubuntu
openssl pkcs12 -in ldaps.pfx -nocerts -nodes -out ldap.key
openssl pkcs12 -in ldaps.pfx -clcerts -nokeys -out ldap.crt
sudo cp ldap.crt /usr/local/share/ca-certificates
sudo update-ca-certificates
Updating certificates in /etc/ssl/certs...
rehash: warning: skipping ca-certificates.crt,it does not contain exactly one certificate or CRL
1 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d...
done.
ll /etc/ssl/certs/ldap.pem
lrwxrwxrwx 1 root root 41 Oct 1 10:20 /etc/ssl/certs/ldap.pem -> /usr/local/share/ca-certificates/ldap.crt
gnutls-cli -p 636 my.local
|<1>| There was a non-CA certificate in the trusted list: CN=myserver.my.local.
Processed 147 CA certificate(s).
Resolving 'my.local:636'...
Connecting to '192.168.0.123:636'...
- Certificate type: X.509
- Got a certificate list of 1 certificates.
- Certificate[0] info:
- subject `CN=myserver.my.local', issuer `CN=my-MYSERVER-CA,DC=my,DC=local', serial 0x750000000212089946907c8e3b000000000002, RSA key 2048 bits, signed using RSA-SHA256, activated `2025-09-30 13:28:52 UTC', expires `2027-09-30 13:38:52 UTC', pin-sha256="ougpnHhxjdx120xX9bN9Y6seqSDtAONKxGCHCAoQYjw="
Public Key ID:
sha1:106bc6bd39fa5897b55316c857d31a30148473d2
sha256:a2e8299c78718ddc75db4c57f5b37d63ab1ea920ed00e34ac46087080a10623c
Public Key PIN:
pin-sha256:ougpnHhxjdx120xX9bN9Y6seqSDtAONKxGCHCAoQYjw=
- Status: The certificate is trusted.
- Successfully sent 0 certificate(s) to server.
- Description: (TLS1.2-X.509)-(ECDHE-SECP384R1)-(RSA-SHA256)-(AES-256-GCM)
- Session ID: A6:1E:00:00:E3:25:0A:AD:E1:33:6B:77:0F:E7:0D:59:3E:D3:9D:01:29:F0:D6:D3:F7:74:B7:00:E3:BF:9C:7A
- Options: extended master secret, safe renegotiation,
- Handshake was completed
- Simple Client Mode:


Securing LDAP over SSL Safely [Windows Server 2019]
https://www.youtube.com/watch?v=8rlk2xDkgLw
It is important that the certificate file has the .crt extension, otherwise it will not be processed.
https://documentation.ubuntu.com/server/how-to/security/install-a-root-ca-certificate-in-the-trust-store/