I cloned repository https://github.com/dockovpn/dockovpn and updated config/server.conf to increase the server log verbosity by setting verb to 4:
port 1194
proto %HOST_TUN_PROTOCOL%
dev tun
ca /etc/openvpn/ca.crt
cert /etc/openvpn/MyReq.crt
key /etc/openvpn/MyReq.key
dh /etc/openvpn/dh.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 208.67.222.222"
push "dhcp-option DNS 208.67.220.220"
duplicate-cn
keepalive 10 120
cipher AES-256-GCM
ncp-ciphers AES-256-GCM:AES-256-CBC
auth SHA512
persist-key
persist-tun
status openvpn-status.log
verb 4
tls-server
tls-version-min 1.2
tls-auth /etc/openvpn/ta.key 0
crl-verify /etc/openvpn/crl.pem
Built and run the docker image:
sudo docker build -t alekslitvinenk/openvpn-verb .
export MY_IP=$(curl -s https://api.ipify.org)
sudo docker run -it --rm --cap-add=NET_ADMIN -p 1194:1194/udp -e HOST_ADDR=$MY_IP --name dockovpn-verb alekslitvinenk/openvpn-verb
the output was the following:
Sun Jan 12 17:28:08 2025 Creating tun/tap device.
Using SSL: openssl OpenSSL 1.1.1t 7 Feb 2023 (Library: OpenSSL 1.1.1k 25 Mar 2021)
Generating RSA private key, 2048 bit long modulus (2 primes)
....+++++
............................+++++
e is 65537 (0x010001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:
CA creation complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/opt/Dockovpn_data/pki/ca.crt
Using SSL: openssl OpenSSL 1.1.1t 7 Feb 2023 (Library: OpenSSL 1.1.1k 25 Mar 2021)
Generating a RSA private key
........................................+++++
......................................................................................+++++
writing new private key to '/opt/Dockovpn_data/pki/easy-rsa-57.nhbOHk/tmp.aKDdmD'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [MyReq]:
Keypair and certificate request completed. Your files are:
req: /opt/Dockovpn_data/pki/reqs/MyReq.req
key: /opt/Dockovpn_data/pki/private/MyReq.key
Using SSL: openssl OpenSSL 1.1.1t 7 Feb 2023 (Library: OpenSSL 1.1.1k 25 Mar 2021)
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a server certificate for 825 days:
subject=
commonName = MyReq
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: Using configuration from /opt/Dockovpn_data/pki/easy-rsa-79.eiIojA/tmp.jApMPN
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'MyReq'
Certificate is to be certified until Apr 17 17:28:08 2027 GMT (825 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /opt/Dockovpn_data/pki/issued/MyReq.crt
2025-01-12 17:28:08 WARNING: Using --genkey --secret filename is DEPRECATED. Use --genkey secret filename instead.
Using SSL: openssl OpenSSL 1.1.1t 7 Feb 2023 (Library: OpenSSL 1.1.1k 25 Mar 2021)
Using configuration from /opt/Dockovpn_data/pki/easy-rsa-143.Jajgmd/tmp.KoCgiD
An updated CRL has been created.
CRL file: /opt/Dockovpn_data/pki/crl.pem
Sun Jan 12 17:28:08 2025 Dockovpn v1.14.0
2025-01-12 17:28:08 Note: Treating option '--ncp-ciphers' as '--data-ciphers' (renamed in OpenVPN 2.5).
2025-01-12 17:28:08 us=361586 WARNING: --topology net30 support for server configs with IPv4 pools will be removed in a future release. Please migrate to --topology subnet as soon as possible.
2025-01-12 17:28:08 us=362000 Current Parameter Settings:
2025-01-12 17:28:08 us=362412 config = '/etc/openvpn/server.conf'
2025-01-12 17:28:08 us=362597 mode = 1
2025-01-12 17:28:08 us=362794 persist_config = DISABLED
2025-01-12 17:28:08 us=363157 persist_mode = 1
2025-01-12 17:28:08 us=363335 show_ciphers = DISABLED
2025-01-12 17:28:08 us=363687 show_digests = DISABLED
2025-01-12 17:28:08 us=363794 show_engines = DISABLED
2025-01-12 17:28:08 us=363910 genkey = DISABLED
2025-01-12 17:28:08 us=363931 genkey_filename = '[UNDEF]'
2025-01-12 17:28:08 us=363947 key_pass_file = '[UNDEF]'
2025-01-12 17:28:08 us=363963 show_tls_ciphers = DISABLED
2025-01-12 17:28:08 us=363978 connect_retry_max = 0
2025-01-12 17:28:08 us=363993 Connection profiles [0]:
2025-01-12 17:28:08 us=364009 proto = udp
2025-01-12 17:28:08 us=364024 local = '[UNDEF]'
2025-01-12 17:28:08 us=364039 local_port = '1194'
2025-01-12 17:28:08 us=364054 remote = '[UNDEF]'
2025-01-12 17:28:08 us=364069 remote_port = '1194'
2025-01-12 17:28:08 us=364084 remote_float = DISABLED
2025-01-12 17:28:08 us=364099 bind_defined = DISABLED
2025-01-12 17:28:08 us=364113 bind_local = ENABLED
2025-01-12 17:28:08 us=364129 bind_ipv6_only = DISABLED
2025-01-12 17:28:08 us=364144 connect_retry_seconds = 5
2025-01-12 17:28:08 us=364158 connect_timeout = 120
2025-01-12 17:28:08 us=364174 socks_proxy_server = '[UNDEF]'
2025-01-12 17:28:08 us=364189 socks_proxy_port = '[UNDEF]'
2025-01-12 17:28:08 us=364204 tun_mtu = 1500
2025-01-12 17:28:08 us=364219 tun_mtu_defined = ENABLED
2025-01-12 17:28:08 us=364234 link_mtu = 1500
2025-01-12 17:28:08 us=364249 link_mtu_defined = DISABLED
2025-01-12 17:28:08 us=364264 tun_mtu_extra = 0
2025-01-12 17:28:08 us=364279 tun_mtu_extra_defined = DISABLED
2025-01-12 17:28:08 us=364294 mtu_discover_type = -1
2025-01-12 17:28:08 us=364308 fragment = 0
2025-01-12 17:28:08 us=364324 mssfix = 1450
2025-01-12 17:28:08 us=364339 explicit_exit_notification = 0
2025-01-12 17:28:08 us=364354 tls_auth_file = '[INLINE]'
2025-01-12 17:28:08 us=364369 key_direction = 0
2025-01-12 17:28:08 us=364384 tls_crypt_file = '[UNDEF]'
2025-01-12 17:28:08 us=364400 tls_crypt_v2_file = '[UNDEF]'
2025-01-12 17:28:08 us=364414 Connection profiles END
2025-01-12 17:28:08 us=364429 remote_random = DISABLED
2025-01-12 17:28:08 us=364444 ipchange = '[UNDEF]'
2025-01-12 17:28:08 us=364459 dev = 'tun'
2025-01-12 17:28:08 us=364478 dev_type = '[UNDEF]'
2025-01-12 17:28:08 us=364502 dev_node = '[UNDEF]'
2025-01-12 17:28:08 us=364518 lladdr = '[UNDEF]'
2025-01-12 17:28:08 us=364534 topology = 1
2025-01-12 17:28:08 us=364548 ifconfig_local = '10.8.0.1'
2025-01-12 17:28:08 us=364563 ifconfig_remote_netmask = '10.8.0.2'
2025-01-12 17:28:08 us=364578 ifconfig_noexec = DISABLED
2025-01-12 17:28:08 us=364593 ifconfig_nowarn = DISABLED
2025-01-12 17:28:08 us=364608 ifconfig_ipv6_local = '[UNDEF]'
2025-01-12 17:28:08 us=364623 ifconfig_ipv6_netbits = 0
2025-01-12 17:28:08 us=364638 ifconfig_ipv6_remote = '[UNDEF]'
2025-01-12 17:28:08 us=364654 shaper = 0
2025-01-12 17:28:08 us=364669 mtu_test = 0
2025-01-12 17:28:08 us=364683 mlock = DISABLED
2025-01-12 17:28:08 us=364698 keepalive_ping = 10
2025-01-12 17:28:08 us=364712 keepalive_timeout = 120
2025-01-12 17:28:08 us=364727 inactivity_timeout = 0
2025-01-12 17:28:08 us=364741 inactivity_minimum_bytes = 0
2025-01-12 17:28:08 us=364756 ping_send_timeout = 10
2025-01-12 17:28:08 us=364773 ping_rec_timeout = 240
2025-01-12 17:28:08 us=364788 ping_rec_timeout_action = 2
2025-01-12 17:28:08 us=364802 ping_timer_remote = DISABLED
2025-01-12 17:28:08 us=364817 remap_sigusr1 = 0
2025-01-12 17:28:08 us=364832 persist_tun = ENABLED
2025-01-12 17:28:08 us=364847 persist_local_ip = DISABLED
2025-01-12 17:28:08 us=364862 persist_remote_ip = DISABLED
2025-01-12 17:28:08 us=364877 persist_key = ENABLED
2025-01-12 17:28:08 us=364891 passtos = DISABLED
2025-01-12 17:28:08 us=364906 resolve_retry_seconds = 1000000000
2025-01-12 17:28:08 us=364921 resolve_in_advance = DISABLED
2025-01-12 17:28:08 us=364937 username = '[UNDEF]'
2025-01-12 17:28:08 us=364952 groupname = '[UNDEF]'
2025-01-12 17:28:08 us=364966 chroot_dir = '[UNDEF]'
2025-01-12 17:28:08 us=364983 cd_dir = '[UNDEF]'
2025-01-12 17:28:08 us=364999 writepid = '[UNDEF]'
2025-01-12 17:28:08 us=365016 up_script = '[UNDEF]'
2025-01-12 17:28:08 us=365031 down_script = '[UNDEF]'
2025-01-12 17:28:08 us=365045 down_pre = DISABLED
2025-01-12 17:28:08 us=365060 up_restart = DISABLED
2025-01-12 17:28:08 us=368449 up_delay = DISABLED
2025-01-12 17:28:08 us=368652 daemon = DISABLED
2025-01-12 17:28:08 us=368835 inetd = 0
2025-01-12 17:28:08 us=369028 log = DISABLED
2025-01-12 17:28:08 us=369201 suppress_timestamps = DISABLED
2025-01-12 17:28:08 us=369235 machine_readable_output = DISABLED
2025-01-12 17:28:08 us=369253 nice = 0
2025-01-12 17:28:08 us=369269 verbosity = 4
2025-01-12 17:28:08 us=369284 mute = 0
2025-01-12 17:28:08 us=369299 gremlin = 0
2025-01-12 17:28:08 us=369314 status_file = 'openvpn-status.log'
2025-01-12 17:28:08 us=369335 status_file_version = 1
2025-01-12 17:28:08 us=369359 status_file_update_freq = 60
2025-01-12 17:28:08 us=369385 occ = ENABLED
2025-01-12 17:28:08 us=369401 rcvbuf = 0
2025-01-12 17:28:08 us=369416 sndbuf = 0
2025-01-12 17:28:08 us=369433 mark = 0
2025-01-12 17:28:08 us=369449 sockflags = 0
2025-01-12 17:28:08 us=369464 fast_io = DISABLED
2025-01-12 17:28:08 us=369479 comp.alg = 0
2025-01-12 17:28:08 us=369494 comp.flags = 0
2025-01-12 17:28:08 us=369509 route_script = '[UNDEF]'
2025-01-12 17:28:08 us=369524 route_default_gateway = '[UNDEF]'
2025-01-12 17:28:08 us=369539 route_default_metric = 0
2025-01-12 17:28:08 us=369553 route_noexec = DISABLED
2025-01-12 17:28:08 us=369568 route_delay = 0
2025-01-12 17:28:08 us=369583 route_delay_window = 30
2025-01-12 17:28:08 us=369598 route_delay_defined = DISABLED
2025-01-12 17:28:08 us=369613 route_nopull = DISABLED
2025-01-12 17:28:08 us=369628 route_gateway_via_dhcp = DISABLED
2025-01-12 17:28:08 us=369643 allow_pull_fqdn = DISABLED
2025-01-12 17:28:08 us=369659 route 10.8.0.0/255.255.255.0/default (not set)/default (not set)
2025-01-12 17:28:08 us=369674 management_addr = '[UNDEF]'
2025-01-12 17:28:08 us=369836 management_port = '[UNDEF]'
2025-01-12 17:28:08 us=369851 management_user_pass = '[UNDEF]'
2025-01-12 17:28:08 us=369866 management_log_history_cache = 250
2025-01-12 17:28:08 us=369881 management_echo_buffer_size = 100
2025-01-12 17:28:08 us=369896 management_write_peer_info_file = '[UNDEF]'
2025-01-12 17:28:08 us=369911 management_client_user = '[UNDEF]'
2025-01-12 17:28:08 us=369926 management_client_group = '[UNDEF]'
2025-01-12 17:28:08 us=369941 management_flags = 0
2025-01-12 17:28:08 us=369956 shared_secret_file = '[UNDEF]'
2025-01-12 17:28:08 us=369971 key_direction = 0
2025-01-12 17:28:08 us=369986 ciphername = 'AES-256-GCM'
2025-01-12 17:28:08 us=370000 ncp_enabled = ENABLED
2025-01-12 17:28:08 us=370015 ncp_ciphers = 'AES-256-GCM:AES-256-CBC'
2025-01-12 17:28:08 us=370031 authname = 'SHA512'
2025-01-12 17:28:08 us=370046 prng_hash = 'SHA1'
2025-01-12 17:28:08 us=370061 prng_nonce_secret_len = 16
2025-01-12 17:28:08 us=370076 keysize = 0
2025-01-12 17:28:08 us=370090 engine = DISABLED
2025-01-12 17:28:08 us=370105 replay = ENABLED
2025-01-12 17:28:08 us=370119 mute_replay_warnings = DISABLED
2025-01-12 17:28:08 us=370134 replay_window = 64
2025-01-12 17:28:08 us=370148 replay_time = 15
2025-01-12 17:28:08 us=370170 packet_id_file = '[UNDEF]'
2025-01-12 17:28:08 us=370191 test_crypto = DISABLED
2025-01-12 17:28:08 us=370207 tls_server = ENABLED
2025-01-12 17:28:08 us=370221 tls_client = DISABLED
2025-01-12 17:28:08 us=370236 ca_file = '/etc/openvpn/ca.crt'
2025-01-12 17:28:08 us=370250 ca_path = '[UNDEF]'
2025-01-12 17:28:08 us=370266 dh_file = '/etc/openvpn/dh.pem'
2025-01-12 17:28:08 us=370281 cert_file = '/etc/openvpn/MyReq.crt'
2025-01-12 17:28:08 us=370296 extra_certs_file = '[UNDEF]'
2025-01-12 17:28:08 us=370311 priv_key_file = '/etc/openvpn/MyReq.key'
2025-01-12 17:28:08 us=370326 pkcs12_file = '[UNDEF]'
2025-01-12 17:28:08 us=370340 cipher_list = '[UNDEF]'
2025-01-12 17:28:08 us=370355 cipher_list_tls13 = '[UNDEF]'
2025-01-12 17:28:08 us=370370 tls_cert_profile = '[UNDEF]'
2025-01-12 17:28:08 us=370384 tls_verify = '[UNDEF]'
2025-01-12 17:28:08 us=370399 tls_export_cert = '[UNDEF]'
2025-01-12 17:28:08 us=370414 verify_x509_type = 0
2025-01-12 17:28:08 us=370429 verify_x509_name = '[UNDEF]'
2025-01-12 17:28:08 us=370444 crl_file = '/etc/openvpn/crl.pem'
2025-01-12 17:28:08 us=370459 ns_cert_type = 0
2025-01-12 17:28:08 us=370474 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370655 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370670 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370685 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370699 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370714 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370729 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370744 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370758 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370773 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370788 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370802 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370817 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370832 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370847 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370862 remote_cert_ku[i] = 0
2025-01-12 17:28:08 us=370877 remote_cert_eku = '[UNDEF]'
2025-01-12 17:28:08 us=370892 ssl_flags = 192
2025-01-12 17:28:08 us=370906 tls_timeout = 2
2025-01-12 17:28:08 us=370921 renegotiate_bytes = -1
2025-01-12 17:28:08 us=370936 renegotiate_packets = 0
2025-01-12 17:28:08 us=370950 renegotiate_seconds = 3600
2025-01-12 17:28:08 us=370970 handshake_window = 60
2025-01-12 17:28:08 us=370985 transition_window = 3600
2025-01-12 17:28:08 us=371001 single_session = DISABLED
2025-01-12 17:28:08 us=371016 push_peer_info = DISABLED
2025-01-12 17:28:08 us=371030 tls_exit = DISABLED
2025-01-12 17:28:08 us=371045 tls_crypt_v2_metadata = '[UNDEF]'
2025-01-12 17:28:08 us=371062 server_network = 10.8.0.0
2025-01-12 17:28:08 us=371077 server_netmask = 255.255.255.0
2025-01-12 17:28:08 us=371094 server_network_ipv6 = ::
2025-01-12 17:28:08 us=371110 server_netbits_ipv6 = 0
2025-01-12 17:28:08 us=371126 server_bridge_ip = 0.0.0.0
2025-01-12 17:28:08 us=371142 server_bridge_netmask = 0.0.0.0
2025-01-12 17:28:08 us=371157 server_bridge_pool_start = 0.0.0.0
2025-01-12 17:28:08 us=371174 server_bridge_pool_end = 0.0.0.0
2025-01-12 17:28:08 us=371189 push_entry = 'redirect-gateway def1 bypass-dhcp'
2025-01-12 17:28:08 us=371204 push_entry = 'dhcp-option DNS 208.67.222.222'
2025-01-12 17:28:08 us=371219 push_entry = 'dhcp-option DNS 208.67.220.220'
2025-01-12 17:28:08 us=371233 push_entry = 'route 10.8.0.1'
2025-01-12 17:28:08 us=371249 push_entry = 'topology net30'
2025-01-12 17:28:08 us=371264 push_entry = 'ping 10'
2025-01-12 17:28:08 us=371279 push_entry = 'ping-restart 120'
2025-01-12 17:28:08 us=371294 ifconfig_pool_defined = ENABLED
2025-01-12 17:28:08 us=371309 ifconfig_pool_start = 10.8.0.4
2025-01-12 17:28:08 us=371325 ifconfig_pool_end = 10.8.0.251
2025-01-12 17:28:08 us=371342 ifconfig_pool_netmask = 0.0.0.0
2025-01-12 17:28:08 us=371357 ifconfig_pool_persist_filename = 'ipp.txt'
2025-01-12 17:28:08 us=371372 ifconfig_pool_persist_refresh_freq = 600
2025-01-12 17:28:08 us=371388 ifconfig_ipv6_pool_defined = DISABLED
2025-01-12 17:28:08 us=371404 ifconfig_ipv6_pool_base = ::
2025-01-12 17:28:08 us=371419 ifconfig_ipv6_pool_netbits = 0
2025-01-12 17:28:08 us=371433 n_bcast_buf = 256
2025-01-12 17:28:08 us=371448 tcp_queue_limit = 64
2025-01-12 17:28:08 us=371463 real_hash_size = 256
2025-01-12 17:28:08 us=371478 virtual_hash_size = 256
2025-01-12 17:28:08 us=371492 client_connect_script = '[UNDEF]'
2025-01-12 17:28:08 us=371508 learn_address_script = '[UNDEF]'
2025-01-12 17:28:08 us=371523 client_disconnect_script = '[UNDEF]'
2025-01-12 17:28:08 us=371539 client_config_dir = '[UNDEF]'
2025-01-12 17:28:08 us=371554 ccd_exclusive = DISABLED
2025-01-12 17:28:08 us=371568 tmp_dir = '/tmp'
2025-01-12 17:28:08 us=371583 push_ifconfig_defined = DISABLED
2025-01-12 17:28:08 us=371598 push_ifconfig_local = 0.0.0.0
2025-01-12 17:28:08 us=371614 push_ifconfig_remote_netmask = 0.0.0.0
2025-01-12 17:28:08 us=371629 push_ifconfig_ipv6_defined = DISABLED
2025-01-12 17:28:08 us=371646 push_ifconfig_ipv6_local = ::/0
2025-01-12 17:28:08 us=371667 push_ifconfig_ipv6_remote = ::
2025-01-12 17:28:08 us=374666 enable_c2c = DISABLED
2025-01-12 17:28:08 us=374878 duplicate_cn = ENABLED
2025-01-12 17:28:08 us=375280 cf_max = 0
2025-01-12 17:28:08 us=375470 cf_per = 0
2025-01-12 17:28:08 us=375662 max_clients = 1024
2025-01-12 17:28:08 us=375845 max_routes_per_client = 256
2025-01-12 17:28:08 us=376473 auth_user_pass_verify_script = '[UNDEF]'
2025-01-12 17:28:08 us=376672 auth_user_pass_verify_script_via_file = DISABLED
2025-01-12 17:28:08 us=376877 auth_token_generate = DISABLED
2025-01-12 17:28:08 us=377172 auth_token_lifetime = 0
2025-01-12 17:28:08 us=377799 auth_token_secret_file = '[UNDEF]'
2025-01-12 17:28:08 us=378012 port_share_host = '[UNDEF]'
2025-01-12 17:28:08 us=378216 port_share_port = '[UNDEF]'
2025-01-12 17:28:08 us=378501 vlan_tagging = DISABLED
2025-01-12 17:28:08 us=378538 vlan_accept = all
2025-01-12 17:28:08 us=378564 vlan_pvid = 1
2025-01-12 17:28:08 us=378588 client = DISABLED
2025-01-12 17:28:08 us=378612 pull = DISABLED
2025-01-12 17:28:08 us=378636 auth_user_pass_file = '[UNDEF]'
2025-01-12 17:28:08 us=378657 OpenVPN 2.5.6 x86_64-alpine-linux-musl [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Mar 24 2022
2025-01-12 17:28:08 us=378686 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10
2025-01-12 17:28:08 us=378747 WARNING: --ifconfig-pool-persist will not work with --duplicate-cn
2025-01-12 17:28:08 us=379480 Diffie-Hellman initialized with 2048 bit key
2025-01-12 17:28:08 us=379892 CRL: loaded 1 CRLs from file /etc/openvpn/crl.pem
2025-01-12 17:28:08 us=379965 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:28:08 us=379984 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:28:08 us=380024 TLS-Auth MTU parms [ L:1621 D:1140 EF:110 EB:0 ET:0 EL:3 ]
2025-01-12 17:28:08 us=380167 ROUTE_GATEWAY 172.17.0.1/255.255.0.0 IFACE=eth0 HWADDR=02:42:ac:11:00:03
2025-01-12 17:28:08 us=380536 TUN/TAP device tun0 opened
2025-01-12 17:28:08 us=380557 do_ifconfig, ipv4=1, ipv6=0
2025-01-12 17:28:08 us=380578 /sbin/ip link set dev tun0 up mtu 1500
2025-01-12 17:28:08 us=385247 /sbin/ip link set dev tun0 up
2025-01-12 17:28:08 us=386305 /sbin/ip addr add dev tun0 local 10.8.0.1 peer 10.8.0.2
2025-01-12 17:28:08 us=388009 /sbin/ip route add 10.8.0.0/24 via 10.8.0.2
2025-01-12 17:28:08 us=391254 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
2025-01-12 17:28:08 us=391490 Could not determine IPv4/IPv6 protocol. Using AF_INET
2025-01-12 17:28:08 us=391734 Socket Buffers: R=[212992->212992] S=[212992->212992]
2025-01-12 17:28:08 us=391954 UDPv4 link local (bound): [AF_INET][undef]:1194
2025-01-12 17:28:08 us=392281 UDPv4 link remote: [AF_UNSPEC]
2025-01-12 17:28:08 us=392476 MULTI: multi_init called, r=256 v=256
2025-01-12 17:28:08 us=392702 IFCONFIG POOL IPv4: base=10.8.0.4 size=62
2025-01-12 17:28:08 us=393069 IFCONFIG POOL LIST
2025-01-12 17:28:08 us=393294 Initialization Sequence Completed
Sun Jan 12 17:28:08 2025 /opt/Dockovpn_data/clients/Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/client.ovpn file has been generated
Sun Jan 12 17:28:08 2025 Config server started, download your client.ovpn config at http://139.162.243.103:80/
Sun Jan 12 17:28:08 2025 NOTE: After you download your client config, http server will be shut down!
Pressed Ctrl+PQ and downloaded the client config:
sudo docker inspect dockovpn-verb | grep IPAddress
wget -O client-verb.ovpn http://172.17.0.3:8080
Attached to the docker container:
sudo docker attach 966f926484bc
Connected from my Windows 10 desktop machine with OpenVPN client and got the following logs at the server side:
2025-01-12 17:31:38 us=927212 MULTI: multi_create_instance called
2025-01-12 17:31:38 us=927402 91.122.37.167:51987 Re-using SSL/TLS context
2025-01-12 17:31:38 us=927712 91.122.37.167:51987 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:31:38 us=927737 91.122.37.167:51987 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:31:38 us=928041 91.122.37.167:51987 Control Channel MTU parms [ L:1621 D:1140 EF:110 EB:0 ET:0 EL:3 ]
2025-01-12 17:31:38 us=928050 91.122.37.167:51987 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
2025-01-12 17:31:38 us=928176 91.122.37.167:51987 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-server'
2025-01-12 17:31:38 us=928182 91.122.37.167:51987 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-client'
2025-01-12 17:31:38 us=928259 91.122.37.167:51987 TLS: Initial packet from [AF_INET]91.122.37.167:51987, sid=d5ee4c3d 2fbbb52e
2025-01-12 17:31:39 us=46860 91.122.37.167:51987 VERIFY OK: depth=1, CN=Easy-RSA CA
2025-01-12 17:31:39 us=46957 91.122.37.167:51987 VERIFY OK: depth=0, CN=Ght7BgpjlktuxxEfj0msScZUmHYxkcgF
2025-01-12 17:31:39 us=47250 91.122.37.167:51987 peer info: IV_VER=2.6.9
2025-01-12 17:31:39 us=47258 91.122.37.167:51987 peer info: IV_PLAT=win
2025-01-12 17:31:39 us=47264 91.122.37.167:51987 peer info: IV_TCPNL=1
2025-01-12 17:31:39 us=47268 91.122.37.167:51987 peer info: IV_MTU=1600
2025-01-12 17:31:39 us=47272 91.122.37.167:51987 peer info: IV_NCP=2
2025-01-12 17:31:39 us=47276 91.122.37.167:51987 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM
2025-01-12 17:31:39 us=47281 91.122.37.167:51987 peer info: IV_PROTO=990
2025-01-12 17:31:39 us=47285 91.122.37.167:51987 peer info: IV_GUI_VER=OpenVPN_GUI_11.47.0.0
2025-01-12 17:31:39 us=47290 91.122.37.167:51987 peer info: IV_SSO=openurl,webauth,crtext
2025-01-12 17:31:39 us=102825 91.122.37.167:51987 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2025-01-12 17:31:39 us=102854 91.122.37.167:51987 [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF] Peer Connection Initiated with [AF_INET]91.122.37.167:51987
2025-01-12 17:31:39 us=102910 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
2025-01-12 17:31:39 us=102944 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: Learn: 10.8.0.6 -> Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987
2025-01-12 17:31:39 us=102953 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: primary virtual IP for Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987: 10.8.0.6
2025-01-12 17:31:39 us=103036 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 17:31:39 us=103045 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 17:31:39 us=103099 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 SENT CONTROL [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF]: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 208.67.222.222,dhcp-option DNS 208.67.220.220,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5,peer-id 0,cipher AES-256-GCM' (status=1)
2025-01-12 17:31:42 us=201212 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=201252 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207910 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207935 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207945 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207957 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207973 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207983 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=207991 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=277249 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=277269 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=277279 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:42 us=462212 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [169.254.98.118], packet dropped
2025-01-12 17:31:43 us=156647 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
2025-01-12 17:31:48 us=155582 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
2025-01-12 17:31:55 us=881031 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
2025-01-12 17:32:12 us=809704 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
2025-01-12 17:32:45 us=753882 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
2025-01-12 17:32:49 us=705038 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
2025-01-12 17:32:57 us=708514 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:51987 MULTI: bad source address from client [], packet dropped
From my Windows 10 desktop machine VPN worked well enough.
Tried to connect from my Android device over 4G and got the following server logs:
2025-01-12 17:53:07 us=389524 MULTI: multi_create_instance called
2025-01-12 17:53:07 us=389664 176.15.163.46:36161 Re-using SSL/TLS context
2025-01-12 17:53:07 us=389811 176.15.163.46:36161 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:53:07 us=389831 176.15.163.46:36161 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:53:07 us=390135 176.15.163.46:36161 Control Channel MTU parms [ L:1621 D:1140 EF:110 EB:0 ET:0 EL:3 ]
2025-01-12 17:53:07 us=390144 176.15.163.46:36161 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
2025-01-12 17:53:07 us=390231 176.15.163.46:36161 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-server'
2025-01-12 17:53:07 us=390240 176.15.163.46:36161 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-client'
2025-01-12 17:53:07 us=390340 176.15.163.46:36161 TLS: Initial packet from [AF_INET]176.15.163.46:36161, sid=3a46eefa cbf9021d
2025-01-12 17:53:07 us=617700 176.15.163.46:36161 VERIFY OK: depth=1, CN=Easy-RSA CA
2025-01-12 17:53:07 us=617809 176.15.163.46:36161 VERIFY OK: depth=0, CN=Ght7BgpjlktuxxEfj0msScZUmHYxkcgF
2025-01-12 17:53:07 us=618222 176.15.163.46:36161 peer info: IV_VER=2.7_master
2025-01-12 17:53:07 us=618231 176.15.163.46:36161 peer info: IV_PLAT=android
2025-01-12 17:53:07 us=618237 176.15.163.46:36161 peer info: IV_TCPNL=1
2025-01-12 17:53:07 us=618241 176.15.163.46:36161 peer info: IV_MTU=1600
2025-01-12 17:53:07 us=618245 176.15.163.46:36161 peer info: IV_NCP=2
2025-01-12 17:53:07 us=618250 176.15.163.46:36161 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
2025-01-12 17:53:07 us=618255 176.15.163.46:36161 peer info: IV_PROTO=2454
2025-01-12 17:53:07 us=622002 176.15.163.46:36161 peer info: IV_LZO_STUB=1
2025-01-12 17:53:07 us=622011 176.15.163.46:36161 peer info: IV_COMP_STUB=1
2025-01-12 17:53:07 us=622015 176.15.163.46:36161 peer info: IV_COMP_STUBv2=1
2025-01-12 17:53:07 us=622020 176.15.163.46:36161 peer info: IV_GUI_VER=de.blinkt.openvpn_0.7.54
2025-01-12 17:53:07 us=622034 176.15.163.46:36161 peer info: IV_SSO=openurl,webauth,crtext
2025-01-12 17:53:07 us=723729 176.15.163.46:36161 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2025-01-12 17:53:07 us=723769 176.15.163.46:36161 [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF] Peer Connection Initiated with [AF_INET]176.15.163.46:36161
2025-01-12 17:53:07 us=723830 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
2025-01-12 17:53:07 us=723866 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: Learn: 10.8.0.6 -> Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161
2025-01-12 17:53:07 us=723874 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: primary virtual IP for Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161: 10.8.0.6
2025-01-12 17:53:07 us=723962 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 17:53:07 us=723970 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 17:53:07 us=724021 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 SENT CONTROL [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF]: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 208.67.222.222,dhcp-option DNS 208.67.220.220,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5,peer-id 0,cipher AES-256-GCM' (status=1)
2025-01-12 17:53:08 us=6834 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=31805 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=36737 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=39843 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=39867 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=111913 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=276728 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=346854 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=349537 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=361722 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=568665 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=624806 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=641804 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=641838 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=953849 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=954173 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:08 us=961605 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:09 us=53684 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:09 us=53711 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:09 us=113871 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:09 us=143714 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:09 us=216689 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:09 us=216713 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=183959 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=183999 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=366989 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=367020 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=983770 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=983820 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:10 us=983834 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:11 us=63710 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:11 us=63748 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:12 us=221846 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:12 us=378698 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:12 us=911681 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:12 us=911709 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:15 us=193710 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:15 us=193742 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:15 us=201607 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:15 us=223952 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:15 us=258722 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:16 us=473893 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:16 us=728675 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:17 us=521873 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:17 us=521899 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:19 us=232848 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 PID_ERR replay-window backtrack occurred [2] [SSL-0] [0__0000000000111222233333333444445555666777777777788889999999>>>] 0:115 0:113 t=1736704399[0] r=[-2,64,15,2,1] sl=[13,64,64,528]
2025-01-12 17:53:23 us=383725 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:23 us=413508 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:23 us=448610 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:24 us=658846 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:25 us=193654 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:26 us=721719 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:26 us=721763 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:38 us=63551 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:38 us=63602 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:39 us=558923 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:39 us=578959 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:41 us=48601 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:43 us=353679 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:45 us=422290 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:45 us=422401 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:58 us=993538 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:53:59 us=347018 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 PID_ERR replay-window backtrack occurred [3] [SSL-0] [00__000000000000000011111111111111111222222222233333333333445566] 0:509 0:506 t=1736704439[0] r=[-2,64,15,3,1] sl=[3,64,64,528]
2025-01-12 17:54:14 us=78724 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:18 us=174141 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:22 us=276883 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:22 us=276951 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:46 us=928807 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:46 us=928865 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:46 us=937765 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:46 us=937805 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:54:46 us=937817 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:55:13 us=360897 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:55:13 us=360955 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:55:25 us=493910 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:55:25 us=494114 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 MULTI: bad source address from client [13.150.182.28], packet dropped
2025-01-12 17:55:38 us=619238 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 17:55:40 us=235488 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 17:55:40 us=602667 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 17:55:41 us=2218 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 17:55:41 us=760613 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 17:55:43 us=285805 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 17:55:46 us=555565 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
tried to connect over WiFi:
2025-01-12 17:59:19 us=196466 MULTI: multi_create_instance called
2025-01-12 17:59:19 us=196569 91.122.37.167:49212 Re-using SSL/TLS context
2025-01-12 17:59:19 us=196670 91.122.37.167:49212 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:59:19 us=196690 91.122.37.167:49212 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 17:59:19 us=196869 91.122.37.167:49212 Control Channel MTU parms [ L:1621 D:1140 EF:110 EB:0 ET:0 EL:3 ]
2025-01-12 17:59:19 us=196908 91.122.37.167:49212 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
2025-01-12 17:59:19 us=197016 91.122.37.167:49212 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,keydir 0,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-server'
2025-01-12 17:59:19 us=197035 91.122.37.167:49212 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-client'
2025-01-12 17:59:19 us=197079 91.122.37.167:49212 TLS: Initial packet from [AF_INET]91.122.37.167:49212, sid=0d5b53f3 abdb5cd6
2025-01-12 17:59:19 us=462697 91.122.37.167:49212 VERIFY OK: depth=1, CN=Easy-RSA CA
2025-01-12 17:59:19 us=462830 91.122.37.167:49212 VERIFY OK: depth=0, CN=Ght7BgpjlktuxxEfj0msScZUmHYxkcgF
2025-01-12 17:59:19 us=468159 91.122.37.167:49212 peer info: IV_VER=2.7_master
2025-01-12 17:59:19 us=468197 91.122.37.167:49212 peer info: IV_PLAT=android
2025-01-12 17:59:19 us=468721 91.122.37.167:49212 peer info: IV_TCPNL=1
2025-01-12 17:59:19 us=468828 91.122.37.167:49212 peer info: IV_MTU=1600
2025-01-12 17:59:19 us=468853 91.122.37.167:49212 peer info: IV_NCP=2
2025-01-12 17:59:19 us=468869 91.122.37.167:49212 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
2025-01-12 17:59:19 us=468884 91.122.37.167:49212 peer info: IV_PROTO=2454
2025-01-12 17:59:19 us=468898 91.122.37.167:49212 peer info: IV_LZO_STUB=1
2025-01-12 17:59:19 us=468912 91.122.37.167:49212 peer info: IV_COMP_STUB=1
2025-01-12 17:59:19 us=468927 91.122.37.167:49212 peer info: IV_COMP_STUBv2=1
2025-01-12 17:59:19 us=468942 91.122.37.167:49212 peer info: IV_GUI_VER=de.blinkt.openvpn_0.7.54
2025-01-12 17:59:19 us=468956 91.122.37.167:49212 peer info: IV_SSO=openurl,webauth,crtext
2025-01-12 17:59:19 us=534932 91.122.37.167:49212 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2025-01-12 17:59:19 us=534998 91.122.37.167:49212 [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF] Peer Connection Initiated with [AF_INET]91.122.37.167:49212
2025-01-12 17:59:19 us=535056 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI_sva: pool returned IPv4=10.8.0.10, IPv6=(Not enabled)
2025-01-12 17:59:19 us=535104 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: Learn: 10.8.0.10 -> Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212
2025-01-12 17:59:19 us=535126 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: primary virtual IP for Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212: 10.8.0.10
2025-01-12 17:59:19 us=535241 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 17:59:19 us=535267 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 17:59:19 us=535313 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 SENT CONTROL [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF]: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 208.67.222.222,dhcp-option DNS 208.67.220.220,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9,peer-id 1,cipher AES-256-GCM' (status=1)
2025-01-12 17:59:19 us=832447 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=832570 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=844943 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=845021 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=845058 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=845090 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=857510 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:19 us=857624 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=73315 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=133746 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=133836 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=318783 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=422027 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=422127 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=818764 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=836748 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=836837 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=859758 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=968302 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:20 us=968379 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:21 us=820216 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:22 us=62481 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:22 us=62532 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:22 us=991414 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:22 us=991491 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:23 us=9325 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:23 us=791207 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:24 us=325795 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:24 us=325853 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:26 us=894773 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:27 us=83870 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:27 us=922821 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:28 us=693391 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:28 us=693441 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:35 us=266396 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:35 us=266510 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:35 us=511878 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 [Ght7BgpjlktuxxEfj0msScZUmHYxkcgF] Inactivity timeout (--ping-restart), restarting
2025-01-12 17:59:35 us=511939 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/176.15.163.46:36161 SIGUSR1[soft,ping-restart] received, client-instance restarting
2025-01-12 17:59:35 us=903590 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:37 us=423547 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:37 us=423574 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:43 us=789596 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 PID_ERR replay-window backtrack occurred [3] [SSL-0] [00__00002333333333344667888999>>>>>>>>>>>>>>>>>>EEEEEEEEEEEEEEEE] 0:111 0:108 t=1736704783[0] r=[-4,64,15,3,1] sl=[17,64,64,528]
2025-01-12 17:59:49 us=852368 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:49 us=871631 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:49 us=871703 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:51 us=724928 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:56 us=98564 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 17:59:56 us=98595 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 18:00:24 us=788197 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 18:00:30 us=890788 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 18:00:30 us=890863 Ght7BgpjlktuxxEfj0msScZUmHYxkcgF/91.122.37.167:49212 MULTI: bad source address from client [192.168.0.181], packet dropped
2025-01-12 18:02:19 us=828419 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:20 us=26740 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:20 us=529991 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:20 us=637948 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:21 us=352326 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:21 us=656870 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:21 us=970285 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:22 us=372817 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:23 us=95945 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:24 us=418293 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:25 us=611 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:27 us=297628 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:29 us=854003 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:32 us=856968 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
2025-01-12 18:02:39 us=672865 read UDPv4 [ECONNREFUSED]: Connection refused (code=111)
The messages like us=828419 read UDPv4 [ECONNREFUSED]: Connection refused (code=111) appeared when I disconnected.
With the both 4G and WiFi VPN connected, but no data was transferred and the browser did not open web pages.
Also I set verb to 4 in client-verb.ovpn and got the following Android client log:
2025-01-12 21:39:30 official build 0.7.54 running on samsung SM-A546E (s5e8835), Android 14 (UP1A.231005.007) API 34, ABI arm64-v8a, (samsung/a54xnsxx/a54x:14/UP1A.231005.007/A546EXXSACXI3:user/release-keys)
2025-01-12 21:39:30 Building configuration…
2025-01-12 21:39:30 Fetched VPN profile (client-verb4) triggered by main profile list
2025-01-12 21:39:30 Scheduling VPN keep alive for VPN client-verb4
2025-01-12 21:39:30 started Socket Thread
2025-01-12 21:39:30 Network Status: CONNECTED to WIFI
2025-01-12 21:39:30 Debug state info: CONNECTED to WIFI , pause: userPause, shouldbeconnected: true, network: SHOULDBECONNECTED
2025-01-12 21:39:30 Debug state info: CONNECTED to WIFI , pause: userPause, shouldbeconnected: true, network: SHOULDBECONNECTED
2025-01-12 21:39:30 P:WARNING: linker: Warning: "/data/app/~~jYbQKF1GxoCjTxZkZ4Nb3g==/de.blinkt.openvpn-STns5KXY6Jlh4_UpD4FFwA==/lib/arm64/libovpnexec.so" is not a directory (ignoring)
2025-01-12 21:39:30 Current Parameter Settings:
2025-01-12 21:39:30 config = 'stdin'
2025-01-12 21:39:30 mode = 0
2025-01-12 21:39:30 show_ciphers = DISABLED
2025-01-12 21:39:30 show_digests = DISABLED
2025-01-12 21:39:30 show_engines = DISABLED
2025-01-12 21:39:30 genkey = DISABLED
2025-01-12 21:39:30 genkey_filename = '[UNDEF]'
2025-01-12 21:39:30 key_pass_file = '[UNDEF]'
2025-01-12 21:39:30 show_tls_ciphers = DISABLED
2025-01-12 21:39:30 connect_retry_max = 0
2025-01-12 21:39:30 Connection profiles [0]:
2025-01-12 21:39:30 proto = udp
2025-01-12 21:39:30 local = '[UNDEF]'
2025-01-12 21:39:30 local_port = '[UNDEF]'
2025-01-12 21:39:30 remote = '139.162.243.103'
2025-01-12 21:39:30 remote_port = '1194'
2025-01-12 21:39:30 remote_float = DISABLED
2025-01-12 21:39:30 bind_defined = DISABLED
2025-01-12 21:39:30 bind_local = DISABLED
2025-01-12 21:39:30 bind_ipv6_only = DISABLED
2025-01-12 21:39:30 connect_retry_seconds = 2
2025-01-12 21:39:30 connect_timeout = 120
2025-01-12 21:39:30 socks_proxy_server = '[UNDEF]'
2025-01-12 21:39:30 socks_proxy_port = '[UNDEF]'
2025-01-12 21:39:30 tun_mtu = 1500
2025-01-12 21:39:30 tun_mtu_defined = ENABLED
2025-01-12 21:39:30 link_mtu = 1500
2025-01-12 21:39:30 link_mtu_defined = DISABLED
2025-01-12 21:39:30 tun_mtu_extra = 0
2025-01-12 21:39:30 tun_mtu_extra_defined = DISABLED
2025-01-12 21:39:30 tls_mtu = 1250
2025-01-12 21:39:30 mtu_discover_type = -1
2025-01-12 21:39:30 fragment = 0
2025-01-12 21:39:30 mssfix = 1492
2025-01-12 21:39:30 mssfix_encap = ENABLED
2025-01-12 21:39:30 mssfix_fixed = DISABLED
2025-01-12 21:39:30 explicit_exit_notification = 0
2025-01-12 21:39:30 tls_auth_file = '[INLINE]'
2025-01-12 21:39:30 key_direction = 1
2025-01-12 21:39:30 tls_crypt_file = '[UNDEF]'
2025-01-12 21:39:30 tls_crypt_v2_file = '[UNDEF]'
2025-01-12 21:39:30 Connection profiles END
2025-01-12 21:39:30 Waiting 0s seconds between connection attempt
2025-01-12 21:39:30 remote_random = DISABLED
2025-01-12 21:39:30 ipchange = '[UNDEF]'
2025-01-12 21:39:30 dev = 'tun'
2025-01-12 21:39:30 dev_type = '[UNDEF]'
2025-01-12 21:39:30 dev_node = '[UNDEF]'
2025-01-12 21:39:30 lladdr = '[UNDEF]'
2025-01-12 21:39:30 topology = 1
2025-01-12 21:39:30 ifconfig_local = '[UNDEF]'
2025-01-12 21:39:30 ifconfig_remote_netmask = '[UNDEF]'
2025-01-12 21:39:30 ifconfig_noexec = DISABLED
2025-01-12 21:39:30 ifconfig_nowarn = ENABLED
2025-01-12 21:39:30 ifconfig_ipv6_local = '[UNDEF]'
2025-01-12 21:39:30 ifconfig_ipv6_netbits = 0
2025-01-12 21:39:30 ifconfig_ipv6_remote = '[UNDEF]'
2025-01-12 21:39:30 shaper = 0
2025-01-12 21:39:30 mtu_test = 0
2025-01-12 21:39:30 mlock = DISABLED
2025-01-12 21:39:30 keepalive_ping = 0
2025-01-12 21:39:30 keepalive_timeout = 0
2025-01-12 21:39:30 inactivity_timeout = 0
2025-01-12 21:39:30 session_timeout = 0
2025-01-12 21:39:30 inactivity_minimum_bytes = 0
2025-01-12 21:39:30 ping_send_timeout = 0
2025-01-12 21:39:30 ping_rec_timeout = 0
2025-01-12 21:39:30 ping_rec_timeout_action = 0
2025-01-12 21:39:30 ping_timer_remote = DISABLED
2025-01-12 21:39:30 remap_sigusr1 = 0
2025-01-12 21:39:30 persist_tun = ENABLED
2025-01-12 21:39:30 persist_local_ip = DISABLED
2025-01-12 21:39:30 persist_remote_ip = DISABLED
2025-01-12 21:39:30 passtos = DISABLED
2025-01-12 21:39:30 resolve_retry_seconds = 1000000000
2025-01-12 21:39:30 resolve_in_advance = ENABLED
2025-01-12 21:39:30 username = '[UNDEF]'
2025-01-12 21:39:30 groupname = '[UNDEF]'
2025-01-12 21:39:30 chroot_dir = '[UNDEF]'
2025-01-12 21:39:30 cd_dir = '[UNDEF]'
2025-01-12 21:39:30 writepid = '[UNDEF]'
2025-01-12 21:39:30 up_script = '[UNDEF]'
2025-01-12 21:39:30 down_script = '[UNDEF]'
2025-01-12 21:39:30 down_pre = DISABLED
2025-01-12 21:39:30 up_restart = DISABLED
2025-01-12 21:39:30 up_delay = DISABLED
2025-01-12 21:39:30 daemon = DISABLED
2025-01-12 21:39:30 log = DISABLED
2025-01-12 21:39:30 suppress_timestamps = DISABLED
2025-01-12 21:39:30 machine_readable_output = ENABLED
2025-01-12 21:39:30 nice = 0
2025-01-12 21:39:30 verbosity = 4
2025-01-12 21:39:30 mute = 0
2025-01-12 21:39:30 gremlin = 0
2025-01-12 21:39:30 status_file = '[UNDEF]'
2025-01-12 21:39:30 status_file_version = 1
2025-01-12 21:39:30 status_file_update_freq = 60
2025-01-12 21:39:30 occ = ENABLED
2025-01-12 21:39:30 rcvbuf = 0
2025-01-12 21:39:30 sndbuf = 0
2025-01-12 21:39:30 sockflags = 0
2025-01-12 21:39:30 fast_io = DISABLED
2025-01-12 21:39:30 comp.alg = 0
2025-01-12 21:39:30 comp.flags = 24
2025-01-12 21:39:30 route_script = '[UNDEF]'
2025-01-12 21:39:30 route_default_gateway = '[UNDEF]'
2025-01-12 21:39:30 route_default_metric = 0
2025-01-12 21:39:30 route_noexec = DISABLED
2025-01-12 21:39:30 route_delay = 0
2025-01-12 21:39:30 route_delay_window = 30
2025-01-12 21:39:30 route_delay_defined = DISABLED
2025-01-12 21:39:30 route_nopull = DISABLED
2025-01-12 21:39:30 route_gateway_via_dhcp = DISABLED
2025-01-12 21:39:30 allow_pull_fqdn = DISABLED
2025-01-12 21:39:30 management_addr = '/data/user/0/de.blinkt.openvpn/cache/mgmtsocket'
2025-01-12 21:39:30 management_port = 'unix'
2025-01-12 21:39:30 management_user_pass = '[UNDEF]'
2025-01-12 21:39:30 management_log_history_cache = 250
2025-01-12 21:39:30 management_echo_buffer_size = 100
2025-01-12 21:39:30 management_client_user = '[UNDEF]'
2025-01-12 21:39:30 management_client_group = '[UNDEF]'
2025-01-12 21:39:30 management_flags = 16678
2025-01-12 21:39:30 shared_secret_file = '[UNDEF]'
2025-01-12 21:39:30 key_direction = 1
2025-01-12 21:39:30 ciphername = 'AES-256-GCM'
2025-01-12 21:39:30 ncp_ciphers = 'AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305'
2025-01-12 21:39:30 authname = 'SHA512'
2025-01-12 21:39:30 engine = DISABLED
2025-01-12 21:39:30 mute_replay_warnings = DISABLED
2025-01-12 21:39:30 replay_window = 64
2025-01-12 21:39:30 replay_time = 15
2025-01-12 21:39:30 packet_id_file = '[UNDEF]'
2025-01-12 21:39:30 test_crypto = DISABLED
2025-01-12 21:39:30 tls_server = DISABLED
2025-01-12 21:39:30 tls_client = ENABLED
2025-01-12 21:39:30 ca_file = '[INLINE]'
2025-01-12 21:39:30 ca_path = '[UNDEF]'
2025-01-12 21:39:30 dh_file = '[UNDEF]'
2025-01-12 21:39:30 cert_file = '[INLINE]'
2025-01-12 21:39:30 extra_certs_file = '[UNDEF]'
2025-01-12 21:39:30 priv_key_file = '[INLINE]'
2025-01-12 21:39:30 pkcs12_file = '[UNDEF]'
2025-01-12 21:39:30 cipher_list = '[UNDEF]'
2025-01-12 21:39:30 cipher_list_tls13 = '[UNDEF]'
2025-01-12 21:39:30 tls_cert_profile = '[UNDEF]'
2025-01-12 21:39:30 tls_verify = '[UNDEF]'
2025-01-12 21:39:30 tls_export_peer_cert_dir = '[UNDEF]'
2025-01-12 21:39:30 verify_x509_type = 0
2025-01-12 21:39:30 verify_x509_name = '[UNDEF]'
2025-01-12 21:39:30 crl_file = '[UNDEF]'
2025-01-12 21:39:30 ns_cert_type = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 65535
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_ku[i] = 0
2025-01-12 21:39:30 remote_cert_eku = 'TLS Web Server Authentication'
2025-01-12 21:39:30 ssl_flags = 192
2025-01-12 21:39:30 tls_timeout = 2
2025-01-12 21:39:30 renegotiate_bytes = -1
2025-01-12 21:39:30 renegotiate_packets = 0
2025-01-12 21:39:30 renegotiate_seconds = 3600
2025-01-12 21:39:30 handshake_window = 60
2025-01-12 21:39:30 transition_window = 3600
2025-01-12 21:39:30 single_session = DISABLED
2025-01-12 21:39:30 push_peer_info = DISABLED
2025-01-12 21:39:30 tls_exit = DISABLED
2025-01-12 21:39:30 tls_crypt_v2_metadata = '[UNDEF]'
2025-01-12 21:39:30 server_network = 0.0.0.0
2025-01-12 21:39:30 server_netmask = 0.0.0.0
2025-01-12 21:39:30 server_network_ipv6 = ::
2025-01-12 21:39:30 server_netbits_ipv6 = 0
2025-01-12 21:39:30 server_bridge_ip = 0.0.0.0
2025-01-12 21:39:30 server_bridge_netmask = 0.0.0.0
2025-01-12 21:39:30 server_bridge_pool_start = 0.0.0.0
2025-01-12 21:39:30 server_bridge_pool_end = 0.0.0.0
2025-01-12 21:39:30 ifconfig_pool_defined = DISABLED
2025-01-12 21:39:30 ifconfig_pool_start = 0.0.0.0
2025-01-12 21:39:30 ifconfig_pool_end = 0.0.0.0
2025-01-12 21:39:30 ifconfig_pool_netmask = 0.0.0.0
2025-01-12 21:39:30 ifconfig_pool_persist_filename = '[UNDEF]'
2025-01-12 21:39:30 ifconfig_pool_persist_refresh_freq = 600
2025-01-12 21:39:30 ifconfig_ipv6_pool_defined = DISABLED
2025-01-12 21:39:30 ifconfig_ipv6_pool_base = ::
2025-01-12 21:39:30 ifconfig_ipv6_pool_netbits = 0
2025-01-12 21:39:30 n_bcast_buf = 256
2025-01-12 21:39:30 tcp_queue_limit = 64
2025-01-12 21:39:30 real_hash_size = 256
2025-01-12 21:39:30 virtual_hash_size = 256
2025-01-12 21:39:30 client_connect_script = '[UNDEF]'
2025-01-12 21:39:30 learn_address_script = '[UNDEF]'
2025-01-12 21:39:30 client_disconnect_script = '[UNDEF]'
2025-01-12 21:39:30 client_crresponse_script = '[UNDEF]'
2025-01-12 21:39:30 client_config_dir = '[UNDEF]'
2025-01-12 21:39:30 ccd_exclusive = DISABLED
2025-01-12 21:39:30 tmp_dir = '/data/data/de.blinkt.openvpn/cache'
2025-01-12 21:39:30 push_ifconfig_defined = DISABLED
2025-01-12 21:39:30 push_ifconfig_local = 0.0.0.0
2025-01-12 21:39:30 push_ifconfig_remote_netmask = 0.0.0.0
2025-01-12 21:39:30 push_ifconfig_ipv6_defined = DISABLED
2025-01-12 21:39:30 push_ifconfig_ipv6_local = ::/0
2025-01-12 21:39:30 push_ifconfig_ipv6_remote = ::
2025-01-12 21:39:30 enable_c2c = DISABLED
2025-01-12 21:39:30 duplicate_cn = DISABLED
2025-01-12 21:39:30 cf_max = 0
2025-01-12 21:39:30 cf_per = 0
2025-01-12 21:39:30 cf_initial_max = 100
2025-01-12 21:39:30 cf_initial_per = 10
2025-01-12 21:39:30 max_clients = 1024
2025-01-12 21:39:30 max_routes_per_client = 256
2025-01-12 21:39:30 auth_user_pass_verify_script = '[UNDEF]'
2025-01-12 21:39:30 auth_user_pass_verify_script_via_file = DISABLED
2025-01-12 21:39:30 auth_token_generate = DISABLED
2025-01-12 21:39:30 force_key_material_export = DISABLED
2025-01-12 21:39:30 auth_token_lifetime = 0
2025-01-12 21:39:30 auth_token_secret_file = '[UNDEF]'
2025-01-12 21:39:30 port_share_host = '[UNDEF]'
2025-01-12 21:39:30 port_share_port = '[UNDEF]'
2025-01-12 21:39:30 vlan_tagging = DISABLED
2025-01-12 21:39:30 vlan_accept = all
2025-01-12 21:39:30 vlan_pvid = 1
2025-01-12 21:39:30 client = ENABLED
2025-01-12 21:39:30 pull = ENABLED
2025-01-12 21:39:30 auth_user_pass_file = '[UNDEF]'
2025-01-12 21:39:30 OpenVPN 2.7-icsopenvpn [git:icsopenvpn/v0.7.54-0-gee0100b4] arm64-v8a [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Dec 4 2024
2025-01-12 21:39:30 library versions: OpenSSL 3.4.0 22 Oct 2024, LZO 2.10
2025-01-12 21:39:30 MANAGEMENT: Connected to management server at /data/user/0/de.blinkt.openvpn/cache/mgmtsocket
2025-01-12 21:39:30 MANAGEMENT: CMD 'version 3'
2025-01-12 21:39:30 MANAGEMENT: CMD 'hold release'
2025-01-12 21:39:30 MANAGEMENT: CMD 'bytecount 2'
2025-01-12 21:39:30 MANAGEMENT: CMD 'state on'
2025-01-12 21:39:30 MANAGEMENT: CMD 'proxy NONE'
2025-01-12 21:39:31 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 21:39:31 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2025-01-12 21:39:31 Control Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1250 tun_max_mtu:0 headroom:126 payload:1600 tailroom:126 ET:0 ]
2025-01-12 21:39:31 Data Channel MTU parms [ mss_fix:0 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ]
2025-01-12 21:39:31 TCP/UDP: Preserving recently used remote address: [AF_INET]139.162.243.103:1194
2025-01-12 21:39:31 Socket Buffers: R=[327680->327680] S=[2805760->2805760]
2025-01-12 21:39:31 MANAGEMENT: CMD 'needok 'PROTECTFD' ok'
2025-01-12 21:39:31 UDPv4 link local: (not bound)
2025-01-12 21:39:31 UDPv4 link remote: [AF_INET]139.162.243.103:1194
2025-01-12 21:39:31 MANAGEMENT: >STATE:1736707171,WAIT,,,,,,
2025-01-12 21:39:31 MANAGEMENT: >STATE:1736707171,AUTH,,,,,,
2025-01-12 21:39:31 TLS: Initial packet from [AF_INET]139.162.243.103:1194, sid=57cb6a2f cb2a16ba
2025-01-12 21:39:32 VERIFY OK: depth=1, CN=Easy-RSA CA
2025-01-12 21:39:32 VERIFY KU OK
2025-01-12 21:39:32 Validating certificate extended key usage
2025-01-12 21:39:32 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2025-01-12 21:39:32 VERIFY EKU OK
2025-01-12 21:39:32 VERIFY OK: depth=0, CN=MyReq
2025-01-12 21:39:32 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bits RSA, signature: RSA-SHA256, peer temporary key: 253 bits X25519, peer signing digest/type: SHA256 RSASSA-PSS
2025-01-12 21:39:32 [MyReq] Peer Connection Initiated with [AF_INET]139.162.243.103:1194
2025-01-12 21:39:32 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1
2025-01-12 21:39:32 TLS: tls_multi_process: initial untrusted session promoted to trusted
2025-01-12 21:39:32 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 208.67.222.222,dhcp-option DNS 208.67.220.220,route 10.8.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9,peer-id 1,cipher AES-256-GCM'
2025-01-12 21:39:32 OPTIONS IMPORT: --ifconfig/up options modified
2025-01-12 21:39:32 OPTIONS IMPORT: route options modified
2025-01-12 21:39:32 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
2025-01-12 21:39:32 ROUTE_GATEWAY 127.100.103.119 IFACE=android-gw
2025-01-12 21:39:32 do_ifconfig, ipv4=1, ipv6=0
2025-01-12 21:39:32 MANAGEMENT: >STATE:1736707172,ASSIGN_IP,,10.8.0.10,,,,
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'IFCONFIG' ok'
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'ROUTE' ok'
2025-01-12 21:39:32 MANAGEMENT: >STATE:1736707172,ADD_ROUTES,,,,,,
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'ROUTE' ok'
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'DNSSERVER' ok'
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'DNSSERVER' ok'
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'PERSIST_TUN_ACTION' OPEN_BEFORE_CLOSE'
2025-01-12 21:39:32 Opening tun interface:
2025-01-12 21:39:32 Local IPv4: 10.8.0.10/30 IPv6: (not set) MTU: 1500
2025-01-12 21:39:32 DNS Server: 208.67.222.222, 208.67.220.220, Domain: null
2025-01-12 21:39:32 Routes: 0.0.0.0/0, 10.8.0.1/32, 10.8.0.8/30
2025-01-12 21:39:32 Routes excluded: 192.168.0.181/24 fe80:0:0:0:34a3:4fff:fe11:f095/64
2025-01-12 21:39:32 Disallowed VPN apps:
2025-01-12 21:39:32 MANAGEMENT: CMD 'needok 'OPENTUN' ok'
2025-01-12 21:39:32 tun/tap device [vpnservice-tun] opened
2025-01-12 21:39:32 Data Channel MTU parms [ mss_fix:1400 max_frag:0 tun_mtu:1500 tun_max_mtu:1600 headroom:136 payload:1768 tailroom:562 ET:0 ]
2025-01-12 21:39:32 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 21:39:32 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2025-01-12 21:39:32 Initialization Sequence Completed
2025-01-12 21:39:32 MANAGEMENT: >STATE:1736707172,CONNECTED,SUCCESS,10.8.0.10,139.162.243.103,1194,,
2025-01-12 21:39:32 Data Channel: cipher 'AES-256-GCM', peer-id: 1
2025-01-12 21:39:32 Timers: ping 10, ping-restart 120
2025-01-12 21:39:32 Debug state info: CONNECTED to WIFI , pause: userPause, shouldbeconnected: true, network: SHOULDBECONNECTED
I am not sure if I selected a right Security Profile in the client app:
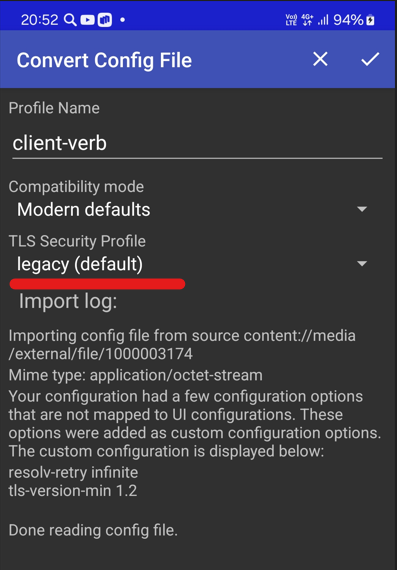
Persisting the configuration
sudo docker-compose up -d
sudo docker inspect dockovpn_dockovpn_1 | grep IPAddress
wget -O client4.ovpn http://172.18.0.2:8080
Generating new client
docker exec dockovpn ./genclient.sh
wget -O client5.ovpn http://172.18.0.2:8080


https://unix.stackexchange.com/questions/40560/how-to-know-if-a-network-interface-is-tap-tun-bridge-or-physical
The answer is to run ethtool -i tunOrTapDeviceName.
$ ethtool -i tapfffb93e9-6a
driver: tun
version: 1.6
firmware-version:
bus-info: tap
supports-statistics: no
supports-test: no
supports-eeprom-access: no
supports-register-dump: no
supports-priv-flags: no
Ubuntu Linux Display List of Ethernet Adapter
https://www.cyberciti.biz/faq/show-ethernet-adapter-ubuntu-linux/
lspci command – List all PCI device including Ethernet cards (NICs) on Linux.
ip command – Display or manipulate routing, devices, policy routing and tunnels on Linux operating systems.
ifconfig command – Display or configure a network interface on Linux or Unix like operating systems.
lshw command – See hardware including list of Ethernet device on Linux.
Where does my traffic go when I use a VPN? Tcpdump shows no outgoing traffic when VPN enabled
https://stackoverflow.com/questions/58918733/where-does-my-traffic-go-when-i-use-a-vpn-tcpdump-shows-no-outgoing-traffic-whe
When you initially capture packets, you are seeing traffic on your default interface (whichever that is). When you enable your VPN, part of the setup process is to make the VPN virtual interface the default interface. Depending on your system, this will mean giving the VPN interface a higher routing metric or higher routing priority in the list.
openvpn server not showing traffic using tcpdump
https://serverfault.com/questions/1052645/openvpn-server-not-showing-traffic-using-tcpdump
and I try to capture traffic using tcpdump -i tun0 icmp –immediate-mode -l -n
How does “restart: always” policy work in docker-compose?
https://serverfault.com/questions/884759/how-does-restart-always-policy-work-in-docker-compose