Add Certificate Manager role
Enable probably something like Certificate Manager role on DC:
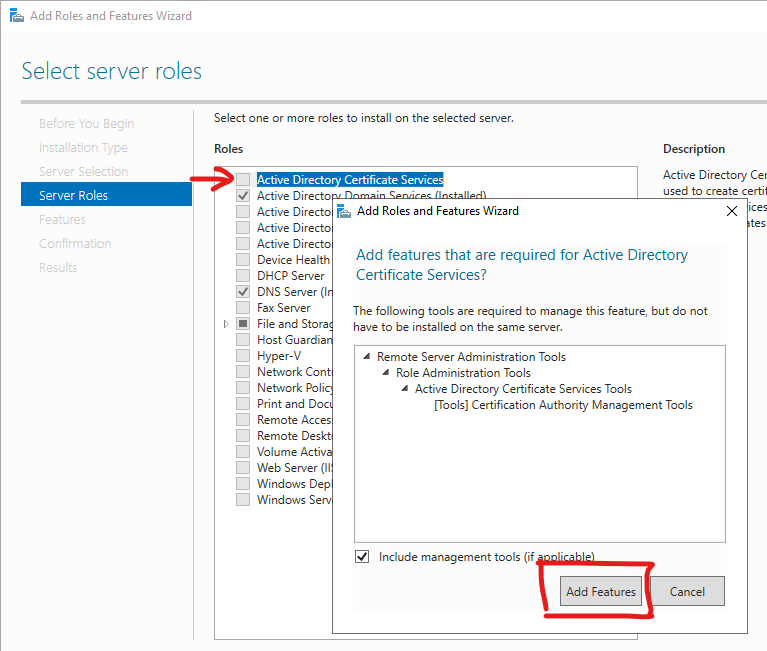
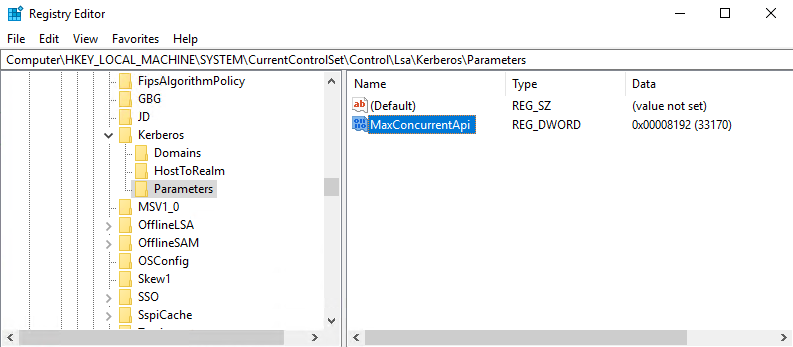
I increased MaxConcurrentApi value of type DWORD in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters:
Right after installing Debian I got the following:
Error: The repository 'cdrom://[Debian GNU/Linux 13.1.0 _Trixie_ - Official amd64 DVD Binary-1 with firmware 20250906-10:24] trixie Release' does not have a Release file.
Notice: Updating from such a repository can't be done securely, and is therefore disabled by default.
Notice: See apt-secure(8) manpage for repository creation and user configuration details.
I fixed this by updating /etc/apt/sources.list as follows:
# deb cdrom:[Debian GNU/Linux 13.1.0 _Trixie_ - Official amd64 DVD Binary-1 with firmware ...] /
deb http://deb.debian.org/debian trixie main contrib non-free-firmware non-free
deb http://deb.debian.org/debian-security trixie-security main contrib non-free-firmware non-free
deb http://deb.debian.org/debian trixie-updates main contrib non-free-firmware non-free
sudo apt update
Tried the following
sysctl net.core.somaxconn
net.core.somaxconn = 4096
sudo sysctl -w net.core.somaxconn=8192
but without a success.
(more…)
python -m pip install frida-tools
Collecting frida-tools
Downloading frida-tools-14.4.5.tar.gz (4.7 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 4.7/4.7 MB 2.8 MB/s 0:00:01
Installing build dependencies ... done
Getting requirements to build wheel ... done
Preparing metadata (pyproject.toml) ... done
Requirement already satisfied: colorama<1.0.0,>=0.2.7 in c:\dev\tools\python313\lib\site-packages (from frida-tools) (0.4.6)
Collecting frida<18.0.0,>=17.2.8 (from frida-tools)
Downloading frida-17.2.17-cp37-abi3-win_amd64.whl.metadata (2.3 kB)
Collecting prompt-toolkit<4.0.0,>=2.0.0 (from frida-tools)
Downloading prompt_toolkit-3.0.52-py3-none-any.whl.metadata (6.4 kB)
Collecting pygments<3.0.0,>=2.0.2 (from frida-tools)
Downloading pygments-2.19.2-py3-none-any.whl.metadata (2.5 kB)
Collecting websockets<14.0.0,>=13.0.0 (from frida-tools)
Downloading websockets-13.1-cp313-cp313-win_amd64.whl.metadata (7.0 kB)
Collecting wcwidth (from prompt-toolkit<4.0.0,>=2.0.0->frida-tools)
Downloading wcwidth-0.2.13-py2.py3-none-any.whl.metadata (14 kB)
Downloading frida-17.2.17-cp37-abi3-win_amd64.whl (41.8 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 41.8/41.8 MB 10.6 MB/s 0:00:04
Downloading prompt_toolkit-3.0.52-py3-none-any.whl (391 kB)
Downloading pygments-2.19.2-py3-none-any.whl (1.2 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 1.2/1.2 MB 10.4 MB/s 0:00:00
Downloading websockets-13.1-cp313-cp313-win_amd64.whl (159 kB)
Downloading wcwidth-0.2.13-py2.py3-none-any.whl (34 kB)
Building wheels for collected packages: frida-tools
Building wheel for frida-tools (pyproject.toml) ... done
Created wheel for frida-tools: filename=frida_tools-14.4.5-py3-none-any.whl size=4699595 sha256=115f2de0f912d70ee9eed25c26b0460f4fe24213359dd46a0ffec3e96e24c911
Stored in directory: c:\users\dmitr\appdata\local\pip\cache\wheels\a6\b2\fb\eff238e22a7ceffee8c7a366ce7ff4011af13c77a103f870d4
Successfully built frida-tools
Installing collected packages: wcwidth, websockets, pygments, prompt-toolkit, frida, frida-tools
━━━━━━━━━━━━━╺━━━━━━━━━━━━━━━━━━━━━━━━━━ 2/6 [pygments] WARNING: The script pygmentize.exe is installed in 'C:\dev\tools\Python313\Scripts' which is not on PATH.
Consider adding this directory to PATH or, if you prefer to suppress this warning, use --no-warn-script-location.
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━╺━━━━━━ 5/6 [frida-tools] WARNING: The scripts frida-apk.exe, frida-compile.exe, frida-create.exe, frida-discover.exe, frida-itrace.exe, frida-join.exe, frida-kill.exe, frida-ls-devices.exe, frida-ls.exe, frida-pm.exe, frida-ps.exe, frida-pull.exe, frida-push.exe, frida-rm.exe, frida-trace.exe and frida.exe are installed in 'C:\dev\tools\Python313\Scripts' which is not on PATH.
Consider adding this directory to PATH or, if you prefer to suppress this warning, use --no-warn-script-location.
Successfully installed frida-17.2.17 frida-tools-14.4.5 prompt-toolkit-3.0.52 pygments-2.19.2 wcwidth-0.2.13 websockets-13.1
Install Nginx with stream module:
sudo apt install nginx-full
The output of the command
nginx -V
should contain with-stream=dynamic.
And add the following to /etc/nginx/nginx.conf:
stream {
server {
listen 12345; # The port that Nginx listens to
proxy_pass 192.168.0.121:389; # Where to forward connections
}
}
Forwarding is disabled by default:
Get-NetIPInterface | Select-Object ifIndex,InterfaceAlias,ConnectionState,Forwarding
ifIndex InterfaceAlias ConnectionState Forwarding
------- -------------- --------------- ----------
57 vEthernet (WSL (Hyper-V firewall)) Connected Disabled
38 vEthernet (Default Switch) Connected Disabled
17 Ethernet 2 Disconnected Disabled
14 Local Area Connection* 10 Disconnected Disabled
22 Local Area Connection* 9 Disconnected Disabled
18 OpenVPN Connect DCO Adapter Disconnected Disabled
7 Wi-Fi Connected Disabled
5 Local Area Connection Disconnected Disabled
1 Loopback Pseudo-Interface 1 Connected Disabled
57 vEthernet (WSL (Hyper-V firewall)) Connected Disabled
38 vEthernet (Default Switch) Connected Disabled
17 Ethernet 2 Disconnected Disabled
14 Local Area Connection* 10 Disconnected Disabled
22 Local Area Connection* 9 Disconnected Disabled
18 OpenVPN Connect DCO Adapter Disconnected Disabled
7 Wi-Fi Connected Disabled
5 Local Area Connection Disconnected Disabled
1 Loopback Pseudo-Interface 1 Connected Disabled
In PowerShell:
wsl --export Ubuntu Ubuntu-01.tar
where Ubuntu is the distro name.
wsl --import UbuntuA C:\Users\dmitriano\wsl\UbuntuA Ubuntu-24.01.tar
probably the folder C:\Users\dmitriano\wsl\UbuntuA should exist.
Download and install latest Go:
wget https://go.dev/dl/go1.25.1.linux-amd64.tar.gz
tar xf ../distrib/go1.25.1.linux-amd64.tar.gz
realpath go
export GOROOT=/home/dmitriano/dev/tools/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$PATH
Install the package:
go install github.com/hamano/lb@latest