I increased MaxConcurrentApi value of type DWORD in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters:
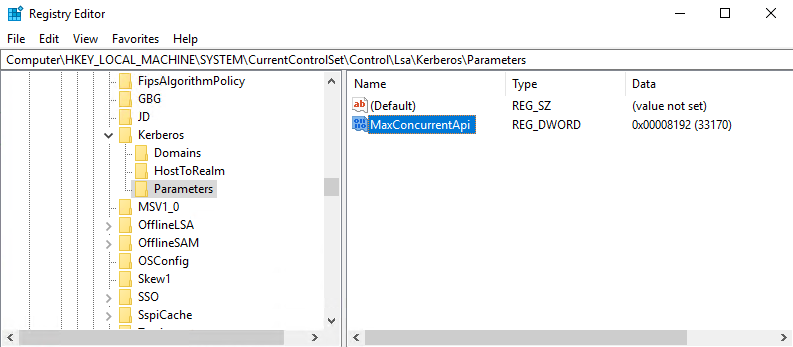
and restarted domain controller.
Updating registry value with PowerShell
# Define the path and value details
$registryPath = "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters"
$valueName = "MaxConcurrentApi"
$newValue = "331700"
# Verify the update
Get-ItemProperty -Path $registryPath | Select-Object $valueName
MaxConcurrentApi
----------------
33170
# Update the registry value
Set-ItemProperty -Path $registryPath -Name $valueName -Value $newValue


https://knowledge.broadcom.com/external/article/169381/when-and-where-to-increase-maxconcurrent.html
The MaxConcurrentAPI is a Windows registry setting:
Registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
Name: MaxConcurrentApi
Type: REG_DWORD
which only needs to be increased on a Domain Controller (DC) if you need to increase NTLM throughput for users from trusted domains, in other words this does not need to be increased if the customer only has a single domain.
https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/kerberos-protocol-registry-kdc-configuration-keys
Kerberos protocol registry entries and KDC configuration keys in Windows