export ad_ip="10.15.7.15"
export ad_user="administrator@itdrde.local"
export ad_password="XXXXXXXXX"
Computers are also Users
ldapsearch -H ldap://$ad_ip:389 -x -D $ad_user -w $ad_password -b "DC=itdrde,DC=local" \
-s sub -a always -z 1000 "(objectClass=user)" "serviceClassName" "serviceDNSName" "objectClass"
Name" "objectClass"
# extended LDIF
#
# LDAPv3
# base <DC=itdrde,DC=local> with scope subtree
# filter: (objectClass=user)
# requesting: serviceClassName serviceDNSName objectClass
#
# Administrator, Users, itdrde.local
dn: CN=Administrator,CN=Users,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
# Guest, Users, itdrde.local
dn: CN=Guest,CN=Users,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
# 7-DEV-DE-DC, Domain Controllers, itdrde.local
dn: CN=7-DEV-DE-DC,OU=Domain Controllers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# krbtgt, Users, itdrde.local
dn: CN=krbtgt,CN=Users,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
# computer1, Domain Controllers, itdrde.local
dn: CN=computer1,OU=Domain Controllers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# computer2, Computers, itdrde.local
dn: CN=computer2,CN=Computers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# computer3, Computers, itdrde.local
dn: CN=computer3,CN=Computers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# computer4, Computers, itdrde.local
dn: CN=computer4,CN=Computers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# computer5, Computers, itdrde.local
dn: CN=computer5,CN=Computers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# computer6, Computers, itdrde.local
dn: CN=computer6,CN=Computers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# computer7, Computers, itdrde.local
dn: CN=computer7,CN=Computers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
# Vasya First, Users, itdrde.local
dn: CN=Vasya First,CN=Users,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
# search reference
ref: ldap://ForestDnsZones.itdrde.local/DC=ForestDnsZones,DC=itdrde,DC=local
# search reference
ref: ldap://DomainDnsZones.itdrde.local/DC=DomainDnsZones,DC=itdrde,DC=local
# search reference
ref: ldap://itdrde.local/CN=Configuration,DC=itdrde,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 16
# numEntries: 12
# numReferences: 3
Querying Domain Controllers via Configuration Context
Domain Controllers that are Global Catalogs
ldapsearch -H ldap://$ad_ip:389 -x -D $ad_user -w $ad_password -b "CN=Configuration,DC=itdrde,DC=local" \
-s sub -a always -z 1000 \
"(&(objectCategory=nTDSDSA)(options:1.2.840.113556.1.4.803:=1))" "objectClass"
# extended LDIF
#
# LDAPv3
# base <CN=Configuration,DC=itdrde,DC=local> with scope subtree
# filter: (&(objectCategory=nTDSDSA)(options:1.2.840.113556.1.4.803:=1))
# requesting: objectClass
#
# NTDS Settings, 7-DEV-DE-DC, Servers, Default-First-Site-Name, Sites, Configur
ation, itdrde.local
dn: CN=NTDS Settings,CN=7-DEV-DE-DC,CN=Servers,CN=Default-First-Site-Name,CN=S
ites,CN=Configuration,DC=itdrde,DC=local
objectClass: top
objectClass: applicationSettings
objectClass: nTDSDSA
# search reference
ref: ldap://itdrde.local/CN=Schema,CN=Configuration,DC=itdrde,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 1
# numReferences: 1
Each DC in a forest has an nTDSDSA object in the config NC:
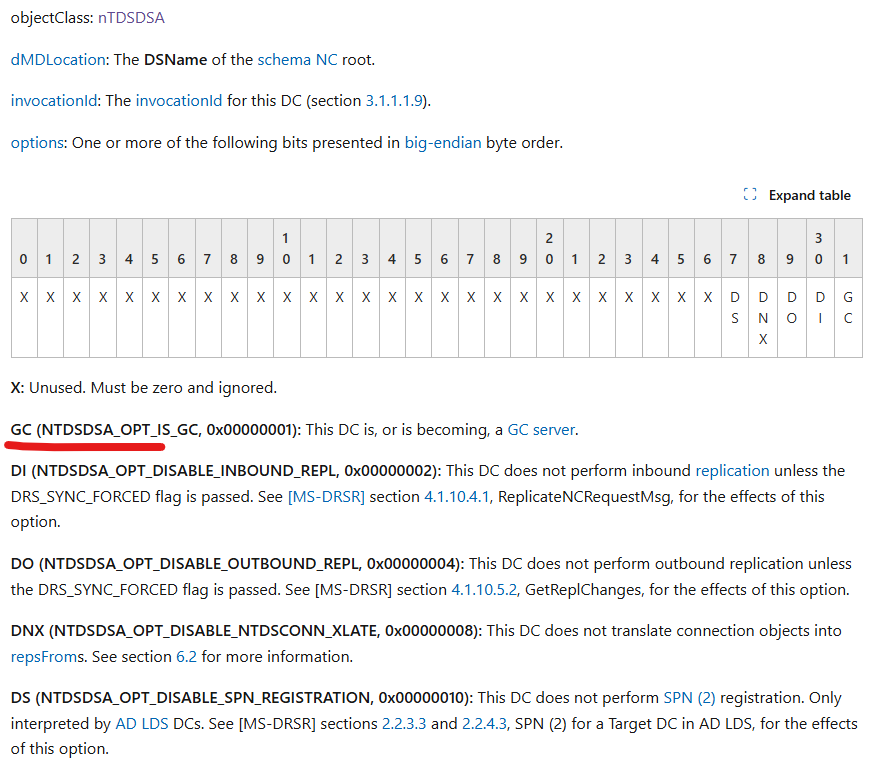
So the query without numeric filter gives the same result:
ldapsearch -H ldap://$ad_ip:389 -x -D $ad_user -w $ad_password -b "CN=Configuration,DC=itdrde,DC=local" \
-s sub -a always -z 1000 \
"(objectCategory=nTDSDSA)" "objectClass"
or
ldapsearch -H ldap://$ad_ip:389 -x -D $ad_user -w $ad_password -b "CN=Configuration,DC=itdrde,DC=local" \
-s sub -a always -z 1000 \
"(objectClass=nTDSDSA)" "objectClass"
Querying Domain Controllers via Domain Context
ldapsearch -H ldap://$ad_ip:389 -x -D $ad_user -w $ad_password -b "DC=itdrde,DC=local" \
-s sub -a always -z 1000 \
"(&(objectCategory=Computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))" "dNSHostName" "objectClass"
# extended LDIF
#
# LDAPv3
# base <DC=itdrde,DC=local> with scope subtree
# filter: (&(objectCategory=Computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))
# requesting: dNSHostName objectClass
#
# 7-DEV-DE-DC, Domain Controllers, itdrde.local
dn: CN=7-DEV-DE-DC,OU=Domain Controllers,DC=itdrde,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
dNSHostName: 7-DEV-DE-DC.itdrde.local
# search reference
ref: ldap://ForestDnsZones.itdrde.local/DC=ForestDnsZones,DC=itdrde,DC=local
# search reference
ref: ldap://DomainDnsZones.itdrde.local/DC=DomainDnsZones,DC=itdrde,DC=local
# search reference
ref: ldap://itdrde.local/CN=Configuration,DC=itdrde,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
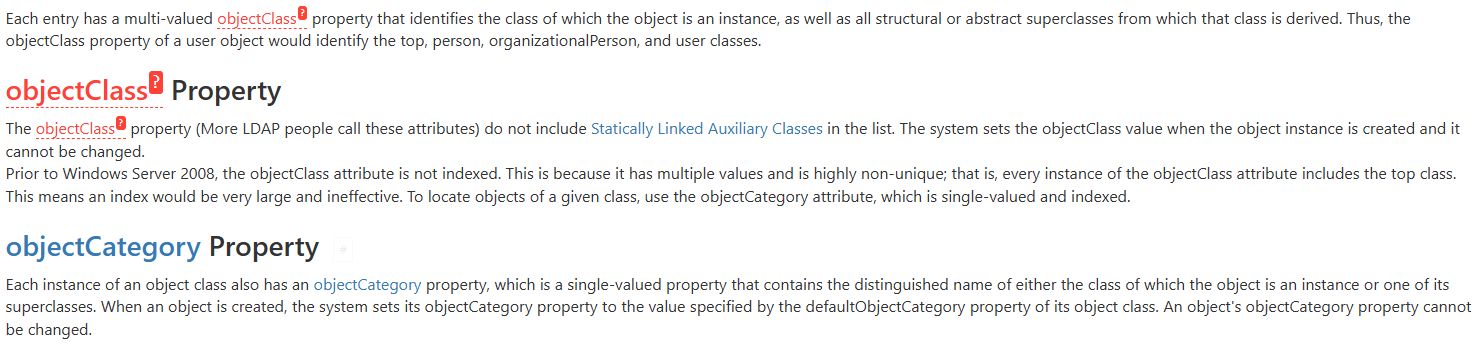
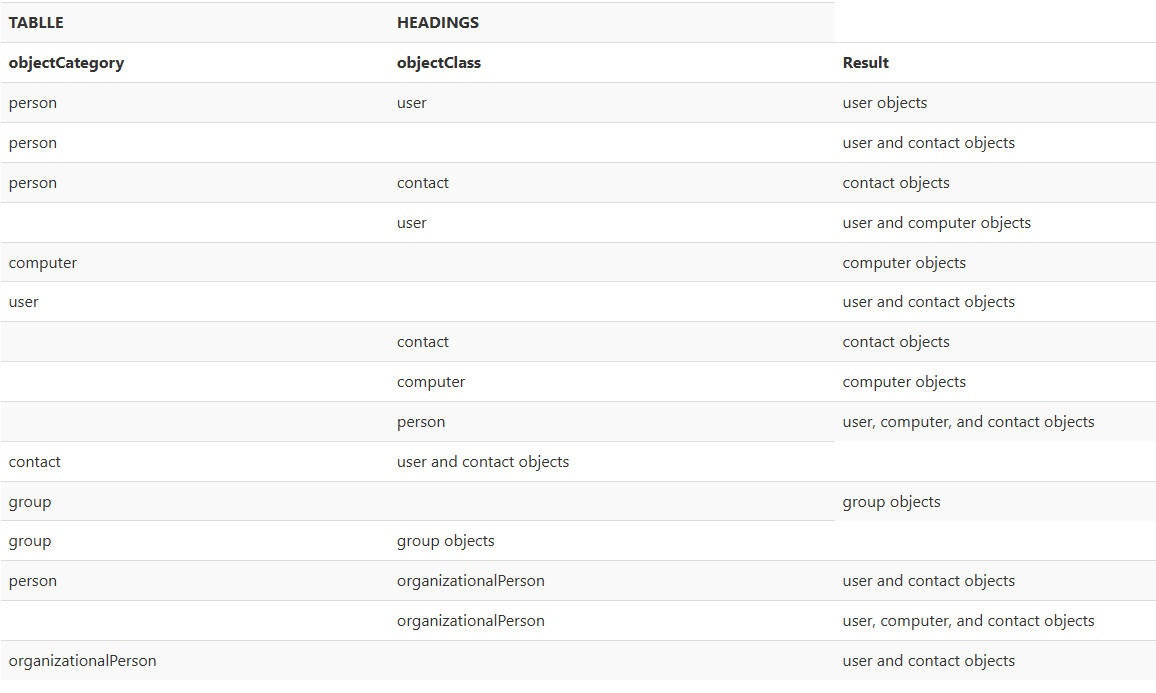
ObjectClass vs ObjectCategory
What does Configuration Context contain?
The Configuration NC is the primary repository for configuration information for a forest.
| Relative Distinguished Name | Description |
|---|---|
| cn=DisplaySpecifiers | Container that holds display specifier objects, which define various properties and functions of the Active Directory MMC Snap-ins. |
| cn=Extended-Rights | Container for extended rights (controlAccessRight) objects. |
| cn=ForestUpdates | Contains objects that are used to represent the state of forest and domain functional level changes. This container is new in Windows Server 2003. |
| cn=LostandFoundConfig | Container for orphaned objects. |
| cn=NTDS Quotas | Container to store quota objects, which are used to restrict the number of objects that security principals can create in a partition or container. This container is new in Windows Server 2003. |
| cn=Partitions | Contains objects for each naming context, application partition, and external reference. |
| cn=Physical Locations | Contains location objects (physicalLocation), … |
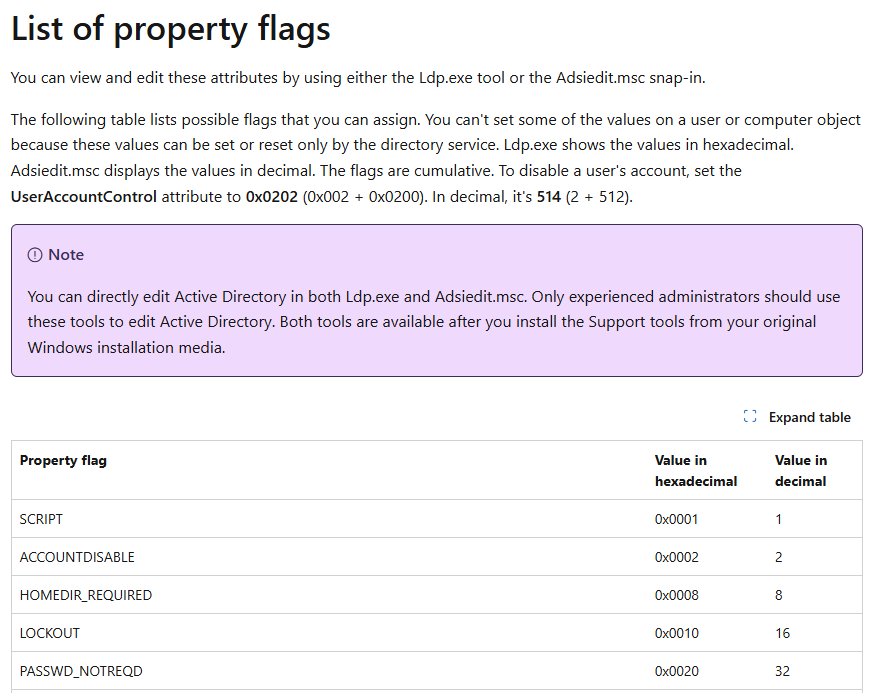
LDAP Matching Rules
| Capability name | OID |
|---|---|
| LDAP_MATCHING_RULE_BIT_AND | 1.2.840.113556.1.4.803 |
| LDAP_MATCHING_RULE_BIT_OR | 1.2.840.113556.1.4.804 |
| LDAP_MATCHING_RULE_TRANSITIVE_EVAL | 1.2.840.113556.1.4.1941 |
| LDAP_MATCHING_RULE_DN_WITH_DATA | 1.2.840.113556.1.4.2253 |

