On the domain controller:
nslookup -q=SRV _kerberos._tcp.other.local
Server: localhost
Address: 127.0.0.1
_kerberos._tcp.other.local SRV service location:
priority = 0
weight = 100
port = 88
svr hostname = 7-dev-de-dc16.other.local
7-dev-de-dc16.other.local internet address = 10.15.7.16
On Linux:
sudo nano /etc/hosts
10.15.7.16 other.local 7-dev-de-dc16.other.local
sudo apt install krb5-user
Updated /etc/krb5.conf as follows:
[libdefaults]
default_realm = OTHER.LOCAL
# The following krb5.conf variables are only for MIT Kerberos.
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
# The following encryption type specification will be used by MIT Kerberos
# if uncommented. In general, the defaults in the MIT Kerberos code are
# correct and overriding these specifications only serves to disable new
# encryption types as they are added, creating interoperability problems.
#
# The only time when you might need to uncomment these lines and change
# the enctypes is if you have local software that will break on ticket
# caches containing ticket encryption types it doesn't know about (such as
# old versions of Sun Java).
# default_tgs_enctypes = des3-hmac-sha1
# default_tkt_enctypes = des3-hmac-sha1
# permitted_enctypes = des3-hmac-sha1
# The following libdefaults parameters are only for Heimdal Kerberos.
fcc-mit-ticketflags = true
ticket_lifetime = 1m
renew_lifetime = 2m
allow_weak_crypto = true
default_tkt_enctypes = camellia128-cts-cmac aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 arcfour-hmac
default_tgs_enctypes = camellia128-cts-cmac aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 arcfour-hmac
permitted_enctypes = camellia128-cts-cmac aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 arcfour-hmac
udp_preference_limit = 1
[realms]
OTHER.LOCAL = {
kdc = 7-dev-de-dc16.other.local
admin_server = 7-dev-de-dc16.other.local
}
ATHENA.MIT.EDU = {
kdc = kerberos.mit.edu
kdc = kerberos-1.mit.edu
kdc = kerberos-2.mit.edu:88
admin_server = kerberos.mit.edu
default_domain = mit.edu
}
ZONE.MIT.EDU = {
kdc = casio.mit.edu
kdc = seiko.mit.edu
admin_server = casio.mit.edu
}
CSAIL.MIT.EDU = {
admin_server = kerberos.csail.mit.edu
default_domain = csail.mit.edu
}
IHTFP.ORG = {
kdc = kerberos.ihtfp.org
admin_server = kerberos.ihtfp.org
}
1TS.ORG = {
kdc = kerberos.1ts.org
admin_server = kerberos.1ts.org
}
ANDREW.CMU.EDU = {
admin_server = kerberos.andrew.cmu.edu
default_domain = andrew.cmu.edu
}
CS.CMU.EDU = {
kdc = kerberos-1.srv.cs.cmu.edu
kdc = kerberos-2.srv.cs.cmu.edu
kdc = kerberos-3.srv.cs.cmu.edu
admin_server = kerberos.cs.cmu.edu
}
DEMENTIA.ORG = {
kdc = kerberos.dementix.org
kdc = kerberos2.dementix.org
admin_server = kerberos.dementix.org
}
stanford.edu = {
kdc = krb5auth1.stanford.edu
kdc = krb5auth2.stanford.edu
kdc = krb5auth3.stanford.edu
master_kdc = krb5auth1.stanford.edu
admin_server = krb5-admin.stanford.edu
default_domain = stanford.edu
}
UTORONTO.CA = {
kdc = kerberos1.utoronto.ca
kdc = kerberos2.utoronto.ca
kdc = kerberos3.utoronto.ca
admin_server = kerberos1.utoronto.ca
default_domain = utoronto.ca
}
[domain_realm]
.mit.edu = ATHENA.MIT.EDU
mit.edu = ATHENA.MIT.EDU
.media.mit.edu = MEDIA-LAB.MIT.EDU
media.mit.edu = MEDIA-LAB.MIT.EDU
.csail.mit.edu = CSAIL.MIT.EDU
csail.mit.edu = CSAIL.MIT.EDU
.whoi.edu = ATHENA.MIT.EDU
whoi.edu = ATHENA.MIT.EDU
.stanford.edu = stanford.edu
.slac.stanford.edu = SLAC.STANFORD.EDU
.toronto.edu = UTORONTO.CA
.utoronto.ca = UTORONTO.CA
.other.local = OTHER.LOCAL
other.local = OTHER.LOCAL
Simple TGT
kinit administrator@OTHER.LOCAL
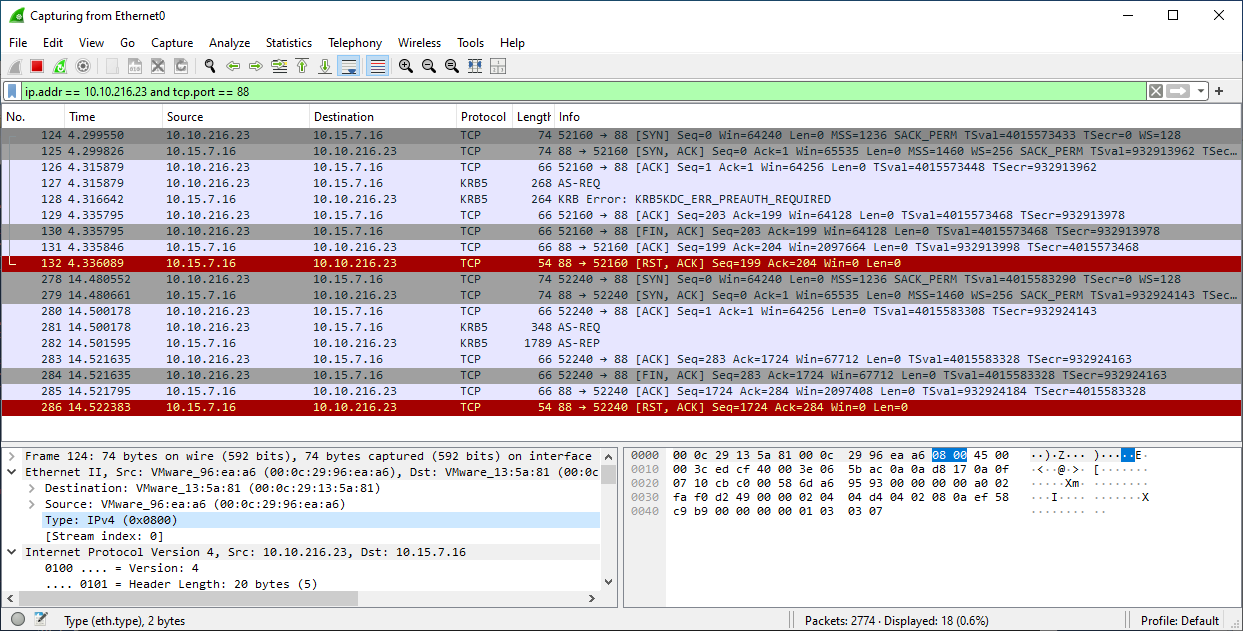
klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: administrator@OTHER.LOCAL
Valid starting Expires Service principal
08/22/25 13:44:29 08/22/25 13:45:29 krbtgt/OTHER.LOCAL@OTHER.LOCAL
renew until 08/22/25 13:46:29
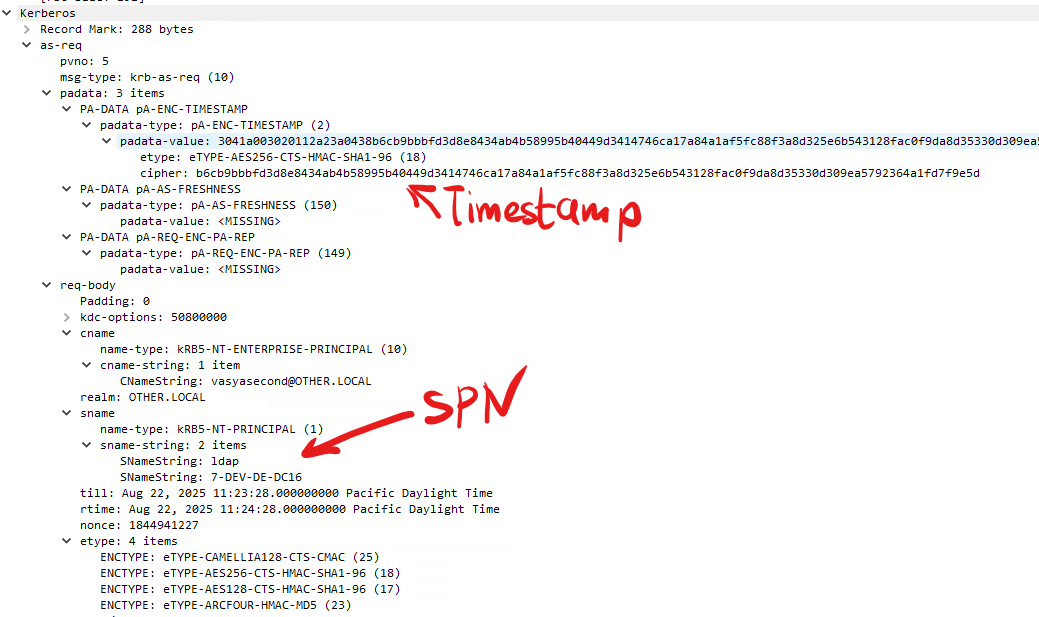
In AS-REQ message the timestamp is encrypted with the client key:
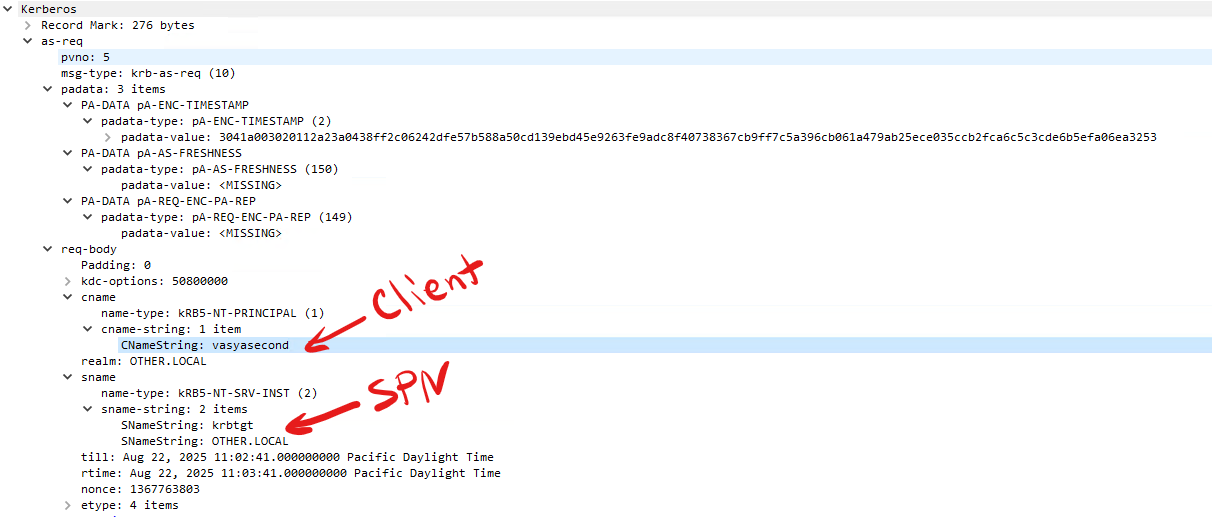
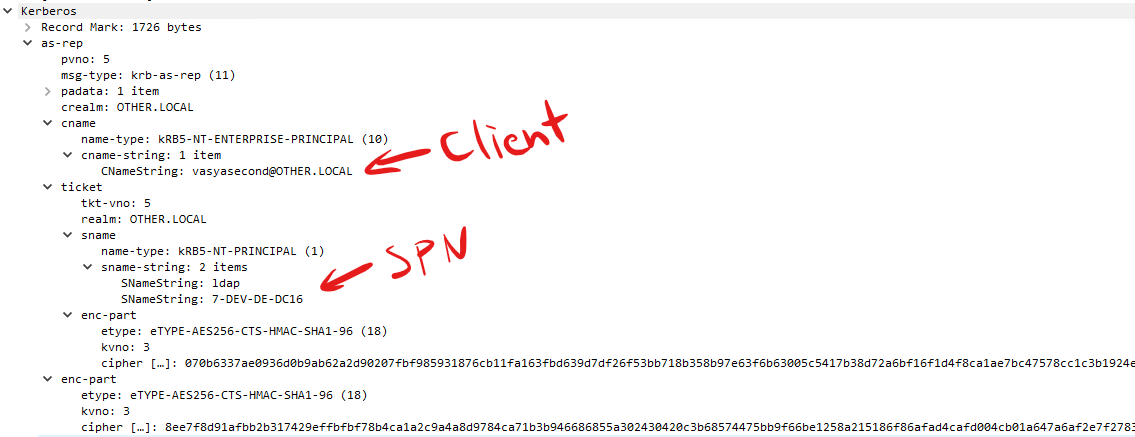
AS-REP message:
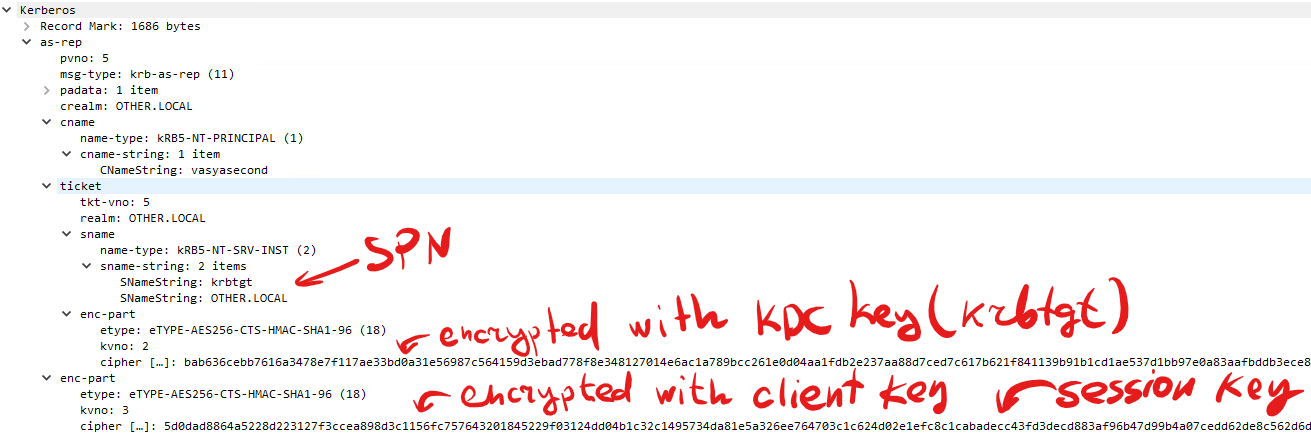
Initial ST
Found SPNs on DC:
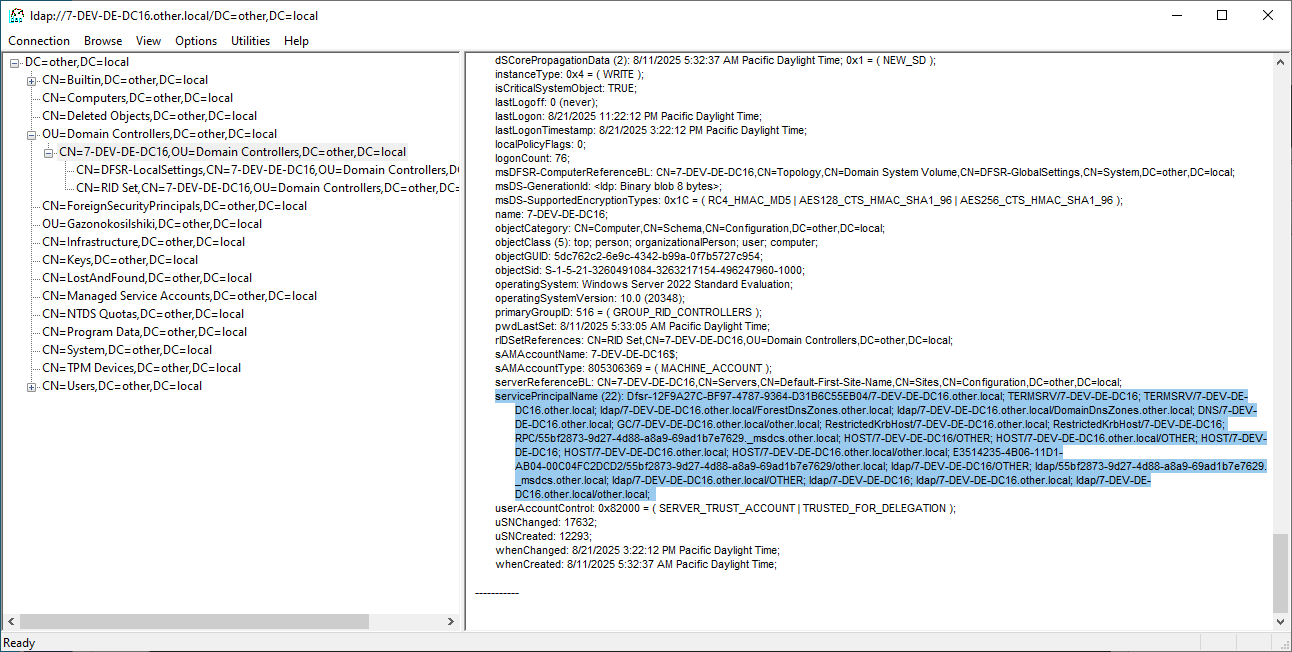
Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/7-DEV-DE-DC16.other.local
TERMSRV/7-DEV-DE-DC16
TERMSRV/7-DEV-DE-DC16.other.local
ldap/7-DEV-DE-DC16.other.local/ForestDnsZones.other.local
ldap/7-DEV-DE-DC16.other.local/DomainDnsZones.other.local
DNS/7-DEV-DE-DC16.other.local
GC/7-DEV-DE-DC16.other.local/other.local
RestrictedKrbHost/7-DEV-DE-DC16.other.local
RestrictedKrbHost/7-DEV-DE-DC16
RPC/55bf2873-9d27-4d88-a8a9-69ad1b7e7629._msdcs.other.local
HOST/7-DEV-DE-DC16/OTHER
HOST/7-DEV-DE-DC16.other.local/OTHER
HOST/7-DEV-DE-DC16
HOST/7-DEV-DE-DC16.other.local
HOST/7-DEV-DE-DC16.other.local/other.local
E3514235-4B06-11D1-AB04-00C04FC2DCD2/55bf2873-9d27-4d88-a8a9-69ad1b7e7629/other.local
ldap/7-DEV-DE-DC16/OTHER
ldap/55bf2873-9d27-4d88-a8a9-69ad1b7e7629._msdcs.other.local
ldap/7-DEV-DE-DC16.other.local/OTHER
ldap/7-DEV-DE-DC16
ldap/7-DEV-DE-DC16.other.local
ldap/7-DEV-DE-DC16.other.local/other.local
kinit -E vasyasecond@OTHER.LOCAL -S ldap/7-DEV-DE-DC16
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: vasyasecond\@OTHER.LOCAL@OTHER.LOCAL
Valid starting Expires Service principal
08/22/25 13:26:50 08/22/25 13:27:50 ldap/7-DEV-DE-DC16@OTHER.LOCAL
renew until 08/22/25 13:28:50
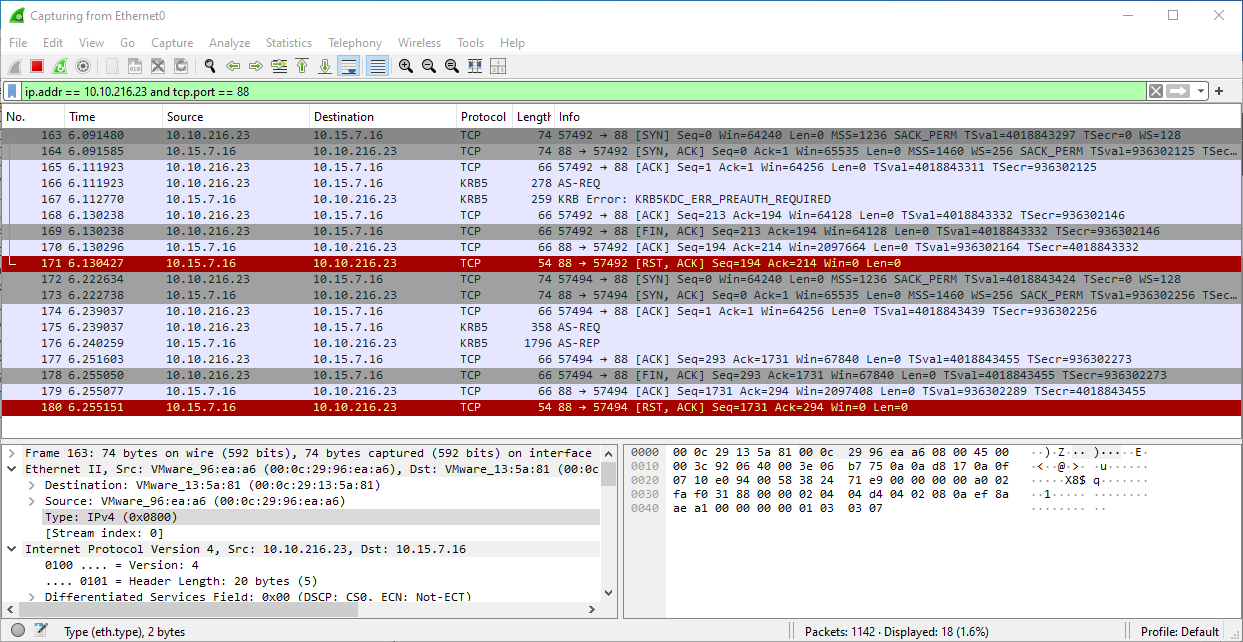
Why there are no TGS-REQ and TGS-REP messages?
AS_REQ message:
AS-REP message:
Renew:
kinit -E vasyasecond@OTHER.LOCAL -S ldap/7-DEV-DE-DC16
kinit -E vasyasecond@OTHER.LOCAL -R -S ldap/7-DEV-DE-DC16
-R works without the password.

