Select network interface:
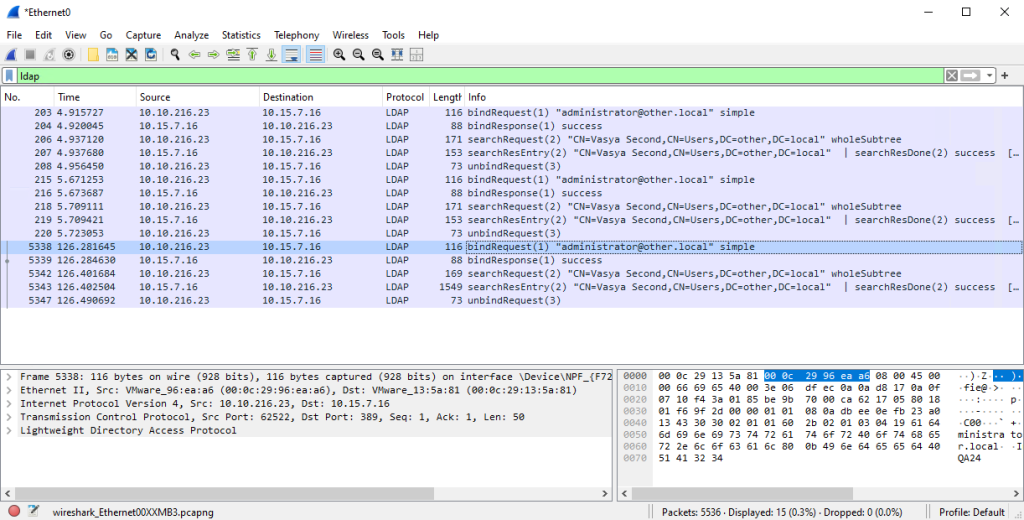
Run the following query from a remote machine:
ldapsearch -H ldap://$ad_ip:389 -x -D $ad_user -w $ad_password -b "CN=Vasya Second,CN=Users,DC=other,DC=local" ntsecuritydescriptor
Capturing loopback traffic
Run ldp.exe on the local machine:
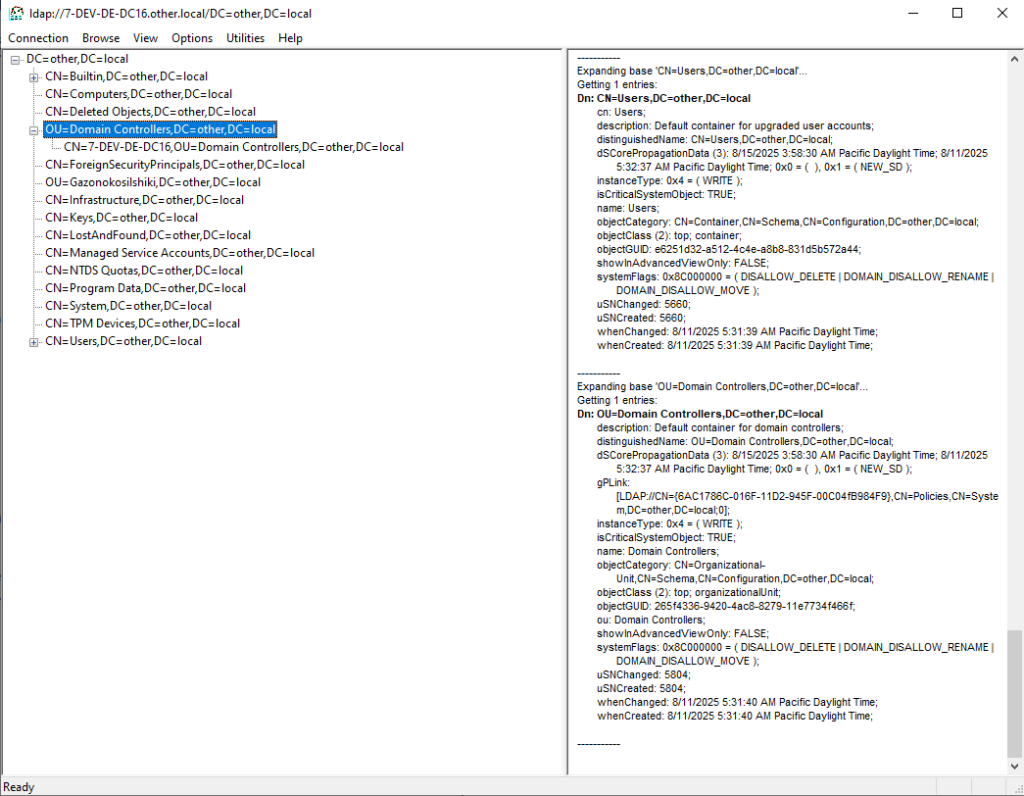
and got the following traffic:
1. Filtering LDAP traffic
- In the filter line in Wireshark, you can use: ldap
- For encrypted LDAPS (usually port 636): tcp.port == 636 But the traffic will be TLS-encrypted, and without keys its contents are not visible.


https://www.youtube.com/watch?v=r0l_54thSYU
Wireshark Packet Sniffing Usernames, Passwords, and Web Pages