Run the docker container:
sudo docker pull openvpn/openvpn-as
sudo ufw allow 1194/udp
sudo ufw allow 943/tcp
sudo ufw allow 1443/tcp
sudo docker run -d --rm \
--name=openvpn-as --device /dev/net/tun \
--cap-add=MKNOD --cap-add=NET_ADMIN \
-p 943:943 -p 1443:443 -p 1194:1194/udp \
-v /var/lib/openvpn-as:/openvpn \
openvpn/openvpn-as
sudo docker logs -f openvpn-as | grep "generated pass"
Auto-generated pass = "*********". Setting in db...
find administrator password and login to Web UI:
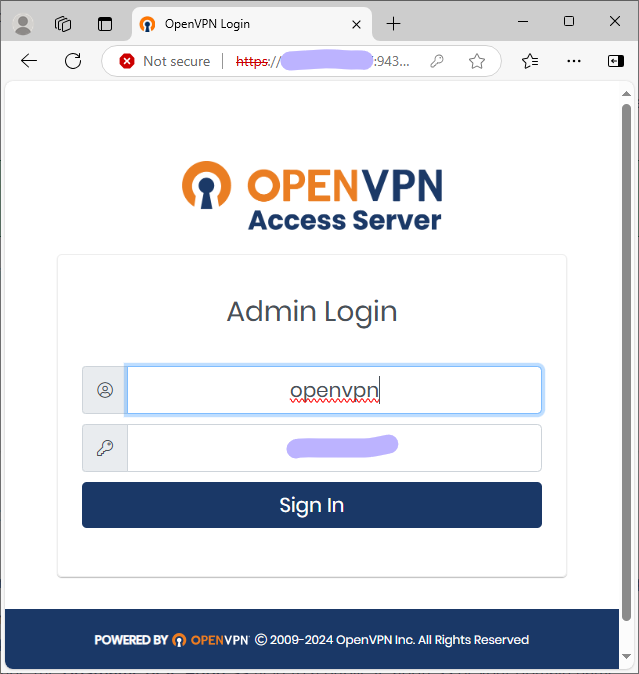
Update server hostname:
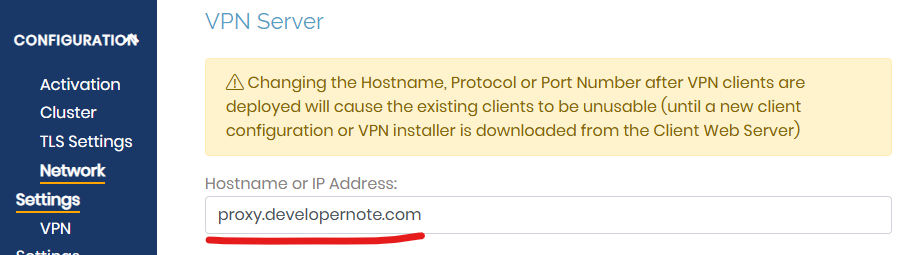
Create a user:
Connect from a client machine as follows:
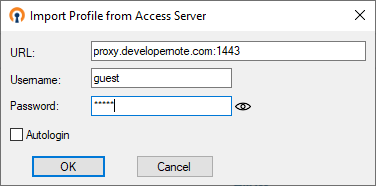
Windows client does not connect with self-signed certificate, but Android clients connects.


Official Docker VPN Server with Access Server | OpenVPN
https://openvpn.net/as-docs/docker.html#sign-in-as-an-administrator
https://askubuntu.com/questions/678215/how-to-restrict-openvpn-clients-to-communicate-with-other-vpn-clients
–client-to-client
Because the OpenVPN server mode handles multiple clients through
a single tun or tap interface, it is effectively a router. The
–client-to-client flag tells OpenVPN to internally route client-
to-client traffic rather than pushing all client-originating
traffic to the TUN/TAP interface.
When this option is used, each client will “see” the other
clients which are currently connected. Otherwise, each client
will only see the server. Don’t use this option if you want to
firewall tunnel traffic using custom, per-client rules.
Managing Access Control in Access Server
https://openvpn.net/as-docs/access-control.html#managing-access-control-in-access-server
OpenVPN client-to-client
When using a TUN (layer 3) OpenVPN server with client-to-client disabled, my clients can still talk to each other.
If client-to-client is enabled, the VPN server forwards client-to-client packets internally without sending them to the IP layer of the host (i.e. to the kernel). The host networking stack does not see those packets at all.